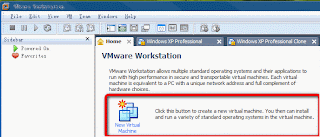
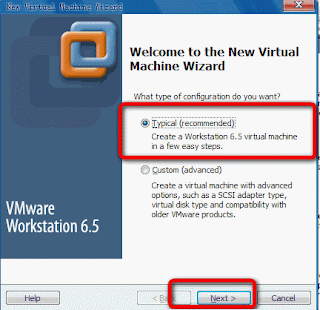
With the use of Microsoft office help user would be able to make a content table under Microsoft word. The procedure can be broadly classified in two steps, where in the first step user have to identify the text which they want to use in the Table of Contents, and in the next step you have to initiate command for the Word to insert the table of content.
After once the Table of content is created user can modify or customize them accordingly. Let's follow simplified procedure of creating a Table of Content.
Step 1: As per Microsoft office help choose the text which you want to use for creating your Table of Contents.
Click within the first major heading that you need to appear in the Table of Contents on your word document. On the paragraph selected assign Heading 1. This is most simple to do, you have click the Style box located on the Formatting toolbar and select Heading 1. Similarly you have to assign Heading 1 style to other significant headings in your document. Use Heading 2 style to sub-headings, Heading 3 style to sub-sub-headings and so on.
However if you want to make any modification on the heading styles look, you can select different font or font size or color.
Step 2: Create the Table of Contents with Microsoft office help. You have to specify the location where you want the table of content to appear. Under Microsoft Word 2002 and 2003 go as follow: Insert > Reference > Index and Tables. Click on the Table of Contents tab. (Elsewhere on this page, this is called the Table of Contents dialog.) Click OK.
In prior version you can do as follow: choose Insert > Index and Tables. Click on the Table of Contents tab. (Elsewhere on this page, this is called the Table of Contents dialog.) Click OK.
Step 3: Customize the Table of Contents as per Microsoft help.
You can bring the changes in the look of your font by modifying the Heading style. Don't make a wrong approach like, Format > Paragraph or Format > Font. Never use the font size or bold buttons on the toolbar.
Alternatively you can do two things in the Table of Contents dialog. Primarily make sure to choose "From Template” that, from the Formats box. Secondary choose the option Modify and modify the relevant TOC style. As per Microsoft help Word uses style TOC 1 for the top level of contents, TOC 2 for the next level etc.
domingo, 27 de diciembre de 2009
Antivirus Program
Antivirus program are the application software coded with an intention to scan any viruses, spyware or malware from your hard disk. They have an efficient scanning engine which can trace any virus as soon as it entered your system. Due to growing broadband users, the chances of virus spreading are more prominent from any emails or attached file. In this blog, we will discuss some important Antivirus Support program which can trace such traffic or virus.
McAfee Total Protection 2010
This is available free over the Internet. It is an award winning Antivirus program, with powerful virus scanning feature. It can scan even the latest virus program "in the wild." After the scan a report is delivered to the user. In addition to virus scan, it also takes backup of all your files when your PC is not in use.
Panda Antivirus Pro 2010
This is an effective Antivirus Support program which can give you comprehensive security against viruses, spyware, rootkits, hackers, online fraud and identity theft. After getting installed you would be able to chat, share photos and videos, bank and buy online, read your favorite blogs or simply surf the web, with complete peace of mind. With the collective Intelligence technology Panda Antivirus Pro 2010 is capable of providing you instant solution.
ClamXav
ClamAV virus scanner provides extensive security from viruses, spyware, rootkits, hackers, online fraud. This is popular commercial antivirus software. Showing good compatibility for both Microsoft and Mac OS.
The above Antivirus Support programs are compatible with the latest Windows 7 (32 and 64-bit) and Processor: Pentium 300 MHz or faster and MS Internet Explorer 6.0.
McAfee Total Protection 2010
This is available free over the Internet. It is an award winning Antivirus program, with powerful virus scanning feature. It can scan even the latest virus program "in the wild." After the scan a report is delivered to the user. In addition to virus scan, it also takes backup of all your files when your PC is not in use.
Panda Antivirus Pro 2010
This is an effective Antivirus Support program which can give you comprehensive security against viruses, spyware, rootkits, hackers, online fraud and identity theft. After getting installed you would be able to chat, share photos and videos, bank and buy online, read your favorite blogs or simply surf the web, with complete peace of mind. With the collective Intelligence technology Panda Antivirus Pro 2010 is capable of providing you instant solution.
ClamXav
ClamAV virus scanner provides extensive security from viruses, spyware, rootkits, hackers, online fraud. This is popular commercial antivirus software. Showing good compatibility for both Microsoft and Mac OS.
The above Antivirus Support programs are compatible with the latest Windows 7 (32 and 64-bit) and Processor: Pentium 300 MHz or faster and MS Internet Explorer 6.0.
Etiquetas:
antivirus
PC Health Check up
PC Health Check up on a regular basis is mandatory to keep up the system performance. PC check up scans the complete systems for any kind of issue related to hardware or software. It will clean up all temporary files and remove any slugs from registry. PC check up works in a discrete manner. It will work only on the assigned task, leaving others absolutely undisturbed. These programs have setting and restore tools which organize the setting of program the way you like.
Let's see some important PC checkup software.
PC Checkup 4.03
This PC Health check up software has been designed in a way to fix multiple PC errors, clean registry, junk files to trigger your system performance. This program will scan your entire system for CPU and Memory usage. It will also diagnose the Disk Drives and Network Adapters in a very visual way. User will also be able to know the supported Operating System information and Applications, Fonts, Drivers or Extensions that are installed.
Norton PC Checkup
Norton PC Health Checkup 2.5 is online scanning software from Norton. If you face any kind of sluggish performance by the system, then you can use this PC checkup to diagnose the issue. It will make a scanning of the entire system and generate a report. The charges of the service 29.99$ will be charge by means of credit card.
PC Pitstop
Above PC Checkup file works very smoothly. This is also an online scanner. After the the complete scan the user will get the detailed reports about performance and PC's health. It will take hardly five minutes to diagnose the issue.
Let's see some important PC checkup software.
PC Checkup 4.03
This PC Health check up software has been designed in a way to fix multiple PC errors, clean registry, junk files to trigger your system performance. This program will scan your entire system for CPU and Memory usage. It will also diagnose the Disk Drives and Network Adapters in a very visual way. User will also be able to know the supported Operating System information and Applications, Fonts, Drivers or Extensions that are installed.
Norton PC Checkup
Norton PC Health Checkup 2.5 is online scanning software from Norton. If you face any kind of sluggish performance by the system, then you can use this PC checkup to diagnose the issue. It will make a scanning of the entire system and generate a report. The charges of the service 29.99$ will be charge by means of credit card.
PC Pitstop
Above PC Checkup file works very smoothly. This is also an online scanner. After the the complete scan the user will get the detailed reports about performance and PC's health. It will take hardly five minutes to diagnose the issue.
Etiquetas:
pc health
Computer troubleshooting
Computer troubleshooting is a dreadful word for most of the users. This is a wide range issue, which may be critical or simple The problem cab be related with the peripheral devices such as associated printer, scanner or other. The actual reason behind writing on computer support is to give simple solution to complex issue.
Startup Issue
Start up is the most common issue in which the user can't get the computer started or it might be starting after some delay. You may be getting error soon after you turn on the computer and screen might be appearing black or blue in extreme condition. All these issues are related to BIOS setting. Hence to do computer troubleshooting you must be very familiar with BIOS settings. You need to turn on the computer and press F8 button. You will be navigated to "Advanced Boot Options" window, which lists several available options. Use your keyboard to select "Last Known Good Configuration," and press "Enter." Now the computer will restart and you will get the registry settings and device drivers which were active when your system was working fine.
However, if you get this kind of issue continuously there is some virus attack and I'll recommend installing any latest Antivirus program.
Slow Performance
There can be plenty of reason for the slow per of your computer. To do the computer optimization you need to, check your start up programs and also the temporary files need to be deleted because they consume unnecessary space of your hard disk. The startup program can be managed from the control panel "Add or Remove" option.
Registry Issue
Computer troubleshooting is very critical in case of any registry issue. So, before making any changes in your Windows registry you must take backup of your computer data. Alternatively some online programs are available that can fix any kind of registry issue. The most common tool for Windows is Cleaner. This provide the safest and easiest way to fix registry problems.
Startup Issue
Start up is the most common issue in which the user can't get the computer started or it might be starting after some delay. You may be getting error soon after you turn on the computer and screen might be appearing black or blue in extreme condition. All these issues are related to BIOS setting. Hence to do computer troubleshooting you must be very familiar with BIOS settings. You need to turn on the computer and press F8 button. You will be navigated to "Advanced Boot Options" window, which lists several available options. Use your keyboard to select "Last Known Good Configuration," and press "Enter." Now the computer will restart and you will get the registry settings and device drivers which were active when your system was working fine.
However, if you get this kind of issue continuously there is some virus attack and I'll recommend installing any latest Antivirus program.
Slow Performance
There can be plenty of reason for the slow per of your computer. To do the computer optimization you need to, check your start up programs and also the temporary files need to be deleted because they consume unnecessary space of your hard disk. The startup program can be managed from the control panel "Add or Remove" option.
Registry Issue
Computer troubleshooting is very critical in case of any registry issue. So, before making any changes in your Windows registry you must take backup of your computer data. Alternatively some online programs are available that can fix any kind of registry issue. The most common tool for Windows is Cleaner. This provide the safest and easiest way to fix registry problems.
Etiquetas:
computer
Windows help
As we know that windows provide a basic platform for all the programs running on the system hence Windows help is of great significance not only to address computer issues but also to get advance features. About 80 percent of the global user are coming from Windows family, so the scope of Windows help has revolutionized in the past decade. Now there are different organization which are involved in providing Windows help.
Windows help to do Mortgage Calculations in a simplified way on your Windows 7 computer. User can calculate the monthly payment, down payment, purchase price, or years of a mortgage. Hence you don't need to take help of any third party software. Let's see how we can manage.
STEP 1. Click the Start button, select "All Programs", "Accessories", then Open the Calculator.
STEP 2. Open the "Mortage Worksheets" pane by selecting "View" - "Worksheets" - "Mortgage".
STEP 3. Underneath "Select the value you want to calculate", click the pull-down and choose from the following:
* Down payment
* Monthly payment
* Purchase price
* Term (years)
STEP 4. Enter the necessary information that will depend on the type of calculation desired. Then click the "Calculate" button.
Let's discuss about some severe computer issue and their best solution from Windows help.
The most common type of issue is related to get logged in when you start your computer. This may happen due to invalid registry entry as a consequence of some virus or spyware attack. User can address this, with the below mention Windows support steps.
STEP 1. Restart the computer and Boot into safe mode.
STEP 2. Click Start, Run and enter regedit into the text box. Hit Enter.
STEP 3. Click on the + sign against, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft \Windows NT\CurrentVersion\Winlogon
STEP 4. Choose the Winlogon folder.
STEP 5. Check the right-hand pane which contains an entry named OldUserinit:
STEP 6. Delete Userinit.
STEP 7. Now rename OldUserinit to Userinit.
STEP 8. Check that the value of Userinit is "C:\WINDOWS\system32\userinit.exe," (the comma at the end of the string is important.)
Important: Modify the path if your Windows folder is not C:\Windows
Windows help to do Mortgage Calculations in a simplified way on your Windows 7 computer. User can calculate the monthly payment, down payment, purchase price, or years of a mortgage. Hence you don't need to take help of any third party software. Let's see how we can manage.
STEP 1. Click the Start button, select "All Programs", "Accessories", then Open the Calculator.
STEP 2. Open the "Mortage Worksheets" pane by selecting "View" - "Worksheets" - "Mortgage".
STEP 3. Underneath "Select the value you want to calculate", click the pull-down and choose from the following:
* Down payment
* Monthly payment
* Purchase price
* Term (years)
STEP 4. Enter the necessary information that will depend on the type of calculation desired. Then click the "Calculate" button.
Let's discuss about some severe computer issue and their best solution from Windows help.
The most common type of issue is related to get logged in when you start your computer. This may happen due to invalid registry entry as a consequence of some virus or spyware attack. User can address this, with the below mention Windows support steps.
STEP 1. Restart the computer and Boot into safe mode.
STEP 2. Click Start, Run and enter regedit into the text box. Hit Enter.
STEP 3. Click on the + sign against, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft \Windows NT\CurrentVersion\Winlogon
STEP 4. Choose the Winlogon folder.
STEP 5. Check the right-hand pane which contains an entry named OldUserinit:
STEP 6. Delete Userinit.
STEP 7. Now rename OldUserinit to Userinit.
STEP 8. Check that the value of Userinit is "C:\WINDOWS\system32\userinit.exe," (the comma at the end of the string is important.)
Important: Modify the path if your Windows folder is not C:\Windows
Etiquetas:
windows help
Computer problems
Computer problems are deeply associated with developing IT industry. Most generic computer problems are often linked with system performance and corruption of operating system. So let's have a look at some of the etiquettes and troubleshooting method to deal with computer problems. If you have Windows XP operating system, then you might be aware of the Desktop cleanup Wizard. The feature of this tool is to remove unused icons from the desktop on the regular basis, this in turns improves the system performance. User can easily enable this Desktop cleanup Wizard from the below steps.
STEP 1. Right-click over the desktop and select Properties.
STEP 2. From the Display Properties dialog box select the Desktop tab.
STEP 3. Select "Customize Desktop."
STEP 4. In the Desktop Items dialog box clear the Run Desktop Cleanup Wizard every 60 days check box.
STEP 5.Click OK to close the dialog boxes
Sometimes your operating system may not be working properly. You may face boot issue issue. To handle this computer problem user have to make an attempt to repair the operating system.
This can be performed with the help of Windows XP Installation CD. Follow the below steps:
STEP 1. Restart the computer with the Windows Installation CD.
STEP 2. Press Enter when you got the message" To setup Windows XP now appears."
STEP 3. Press Enter when you get Welcome screen of Setup.
STEP 4. Press F8 to agree against the Windows XP Licensing Agreement.
STEP 5. Press R to repair Windows XP.
STEP 6. Follow the repair installation instruction.
Unable to get logon on the computer Windows is another serious computer problem. This may happen due to invalid registry entry as a consequence of some virus or spyware attack. User can address this computer problem with the below mention steps.
STEP 1. Restart the computer and Boot into safe mode.
STEP 2. Click Start, Run and enter regedit into the text box. Hit Enter.
STEP 3. Click on the + sign against, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft \Windows NT\CurrentVersion\Winlogon
STEP 4. Choose the Winlogon folder.
STEP 5. Check the right-hand pane which contains an entry named OldUserinit:
STEP 6. Delete Userinit.
STEP 7. Now rename OldUserinit to Userinit.
STEP 8. Check that the value of Userinit is "C:\WINDOWS\system32\userinit.exe," (the comma at the end of the string is important.)
Important: Modify the path if your Windows folder is not C:\Windows.
STEP 1. Right-click over the desktop and select Properties.
STEP 2. From the Display Properties dialog box select the Desktop tab.
STEP 3. Select "Customize Desktop."
STEP 4. In the Desktop Items dialog box clear the Run Desktop Cleanup Wizard every 60 days check box.
STEP 5.Click OK to close the dialog boxes
Sometimes your operating system may not be working properly. You may face boot issue issue. To handle this computer problem user have to make an attempt to repair the operating system.
This can be performed with the help of Windows XP Installation CD. Follow the below steps:
STEP 1. Restart the computer with the Windows Installation CD.
STEP 2. Press Enter when you got the message" To setup Windows XP now appears."
STEP 3. Press Enter when you get Welcome screen of Setup.
STEP 4. Press F8 to agree against the Windows XP Licensing Agreement.
STEP 5. Press R to repair Windows XP.
STEP 6. Follow the repair installation instruction.
Unable to get logon on the computer Windows is another serious computer problem. This may happen due to invalid registry entry as a consequence of some virus or spyware attack. User can address this computer problem with the below mention steps.
STEP 1. Restart the computer and Boot into safe mode.
STEP 2. Click Start, Run and enter regedit into the text box. Hit Enter.
STEP 3. Click on the + sign against, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft \Windows NT\CurrentVersion\Winlogon
STEP 4. Choose the Winlogon folder.
STEP 5. Check the right-hand pane which contains an entry named OldUserinit:
STEP 6. Delete Userinit.
STEP 7. Now rename OldUserinit to Userinit.
STEP 8. Check that the value of Userinit is "C:\WINDOWS\system32\userinit.exe," (the comma at the end of the string is important.)
Important: Modify the path if your Windows folder is not C:\Windows.
Etiquetas:
computer
Windows 7 Guide- 5 Tricks You Must Know
If you belive that you know everything about Windows 7 then think twice. Windows 7 is latest operating system there are still few things that you must know to enhance your knowledge.
Pin your folder to Windows 7 Taskbar: Most of the users want to access folders quickly on desktop. In Windows 7 users can add the computer menu as a folder on the taskbar for the quickest access to their folders.
● In order to add a folder to the taskbar, just right-click on the taskbar and choose the Toolbars menu, and then click on New Toolbar.
● Locate the folder that you want. Now you can see your folder right there on the taskbar.
How to Prevent Windows update from automatically restarting your Windows 7 computer?: As we all know that Windows always prompts to restart computer whenever it detects any changes. There's a couple of ways that we can this behavior. However, you'll still get the prompts, but it won't force you to shut down or restart.
● Open up regedit.exe through the start menu search box or run dialog, and navigate down to the following key, HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
● Create a new 32-bit DWORD value named NoAutoRebootWithLoggedOnUsers and give it a value of 1 to prevent automatic reboot while users are logged on. Delete the value to put things back to the way they were.
How to Log On Automatically in Windows 7?: If you are the only single person using your computer at home or office, then save your precious time while login. There is one way to make sure that Windows doesn't prompt you for a password when you log on.
● Type in netplwiz into the start menu search box, press Enter.
● On next screen uncheck the box that says "Users must enter a user name and password to use this computer", and then hit Apply. You'll see a username and password box. Enter in the appropriate information here and click OK.
Turn on Remote Desktop on Windows 7 computer: This tool is not available with all editions of Windows 7. By default, you can access it if you have Windows 7 Ultimate, Pro, or Business editions.
STEP 1: You can either right-click the Computer icon and choose properties, or you can type in system into the start menu search box, and then find the entry for System.
STEP 2: Click the Remote Settings link and enable this option.
Add an additional clock: Windows 7 provides a new feature that allows you to set different time zones on a single computer. You can add one or two additional clocks to the Windows Taskbar. It would help you while contacting people, who stay in different cities or countries.
Steps to perform this task:
1. Click on the Taskbar clock and click “Change date and time settings”
2. On Next screen click the “Additional Clocks” tab.
3. Click “Show this clock” next to the first clock.
4. Next, click on the “Select time zone” pull-down to choose the desired time zone for the clock.
5. Next, “Enter display name”, give a name for your clock that will appear when you navigate your mouse over the Taskbar clock or click the Taskbar clock to show the larger clocks.
6. Repeat steps 3-5 for the second clock if you wish to add a second clock to the Windows 7 Taskbar.
7. Click “OK” to close the dialog box.
Pin your folder to Windows 7 Taskbar: Most of the users want to access folders quickly on desktop. In Windows 7 users can add the computer menu as a folder on the taskbar for the quickest access to their folders.
● In order to add a folder to the taskbar, just right-click on the taskbar and choose the Toolbars menu, and then click on New Toolbar.
● Locate the folder that you want. Now you can see your folder right there on the taskbar.
How to Prevent Windows update from automatically restarting your Windows 7 computer?: As we all know that Windows always prompts to restart computer whenever it detects any changes. There's a couple of ways that we can this behavior. However, you'll still get the prompts, but it won't force you to shut down or restart.
● Open up regedit.exe through the start menu search box or run dialog, and navigate down to the following key, HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
● Create a new 32-bit DWORD value named NoAutoRebootWithLoggedOnUsers and give it a value of 1 to prevent automatic reboot while users are logged on. Delete the value to put things back to the way they were.
How to Log On Automatically in Windows 7?: If you are the only single person using your computer at home or office, then save your precious time while login. There is one way to make sure that Windows doesn't prompt you for a password when you log on.
● Type in netplwiz into the start menu search box, press Enter.
● On next screen uncheck the box that says "Users must enter a user name and password to use this computer", and then hit Apply. You'll see a username and password box. Enter in the appropriate information here and click OK.
Turn on Remote Desktop on Windows 7 computer: This tool is not available with all editions of Windows 7. By default, you can access it if you have Windows 7 Ultimate, Pro, or Business editions.
STEP 1: You can either right-click the Computer icon and choose properties, or you can type in system into the start menu search box, and then find the entry for System.
STEP 2: Click the Remote Settings link and enable this option.
Add an additional clock: Windows 7 provides a new feature that allows you to set different time zones on a single computer. You can add one or two additional clocks to the Windows Taskbar. It would help you while contacting people, who stay in different cities or countries.
Steps to perform this task:
1. Click on the Taskbar clock and click “Change date and time settings”
2. On Next screen click the “Additional Clocks” tab.
3. Click “Show this clock” next to the first clock.
4. Next, click on the “Select time zone” pull-down to choose the desired time zone for the clock.
5. Next, “Enter display name”, give a name for your clock that will appear when you navigate your mouse over the Taskbar clock or click the Taskbar clock to show the larger clocks.
6. Repeat steps 3-5 for the second clock if you wish to add a second clock to the Windows 7 Taskbar.
7. Click “OK” to close the dialog box.
Etiquetas:
windows 7
Windows vista help
Prior to the launch of any version of windows Microsoft get ready with its gun to handle any adverse condition. Similar is the case to Windows Vista launch. Microsoft has provided Windows Vista compatibility Center to address any unfair situation. In fact this is a very responsible step on behalf of Microsoft, so that the users don't have to suffer while making selection regarding any software or hardware.
Windows Vista Compatibility Center is a common platform which brings together Microsoft, other manufacturer and customers. The manufacturers of various hardware and softwares come with all the details of their products so that user can get right information about them before investing a single penny. To assure the retail user Microsoft has also put its logos over the suitable products.
Look to this extensive collection of compatibility information when you upgrade to the Windows Vista operating system. And when you're ready for a new PC, you'll find the downloads you need to run your favorite software and devices. The "Works with Windows Vista" logo indicates that particular product is reliables and tested with Windows Vista. Hence Windows Vista Compatibility Center can also be consider as
Windows Vista Help.
Windows Vista Solution Center is the other significant user-friendly Windows Vista Help platform developed by Microsoft. This platform is to address adverse situation. Any kind of issue be it relates with the hardware or software compatibility, Windows Vista Help has real-time solution. Here the user will get the different categories of issues starting from the Top issues, Install, Upgrade, Performance, Maintenance, Programs, e-mails, Security and Privacy, Networking and so on. Hence nothing is out of scope from Microsoft windows vista support.
After getting the suggestion and implementing those, user can write comments to further improve Windows Vista Help.
Windows Vista Compatibility Center is a common platform which brings together Microsoft, other manufacturer and customers. The manufacturers of various hardware and softwares come with all the details of their products so that user can get right information about them before investing a single penny. To assure the retail user Microsoft has also put its logos over the suitable products.
Look to this extensive collection of compatibility information when you upgrade to the Windows Vista operating system. And when you're ready for a new PC, you'll find the downloads you need to run your favorite software and devices. The "Works with Windows Vista" logo indicates that particular product is reliables and tested with Windows Vista. Hence Windows Vista Compatibility Center can also be consider as
Windows Vista Help.
Windows Vista Solution Center is the other significant user-friendly Windows Vista Help platform developed by Microsoft. This platform is to address adverse situation. Any kind of issue be it relates with the hardware or software compatibility, Windows Vista Help has real-time solution. Here the user will get the different categories of issues starting from the Top issues, Install, Upgrade, Performance, Maintenance, Programs, e-mails, Security and Privacy, Networking and so on. Hence nothing is out of scope from Microsoft windows vista support.
After getting the suggestion and implementing those, user can write comments to further improve Windows Vista Help.
Etiquetas:
windows vista
Virus removal
Viruses are the man made software coding that attacks your system or application softwares. They are hazardous for your computer system and eventually to the stored data. Even they can steal your personal information like password and credit card information. So virus removal is important to maintain privacy of personal information and keep system working in smooth condition.
Virus removal softwares are available in two modes, the first one is the independent or third party software and other is online scanner. Both differ considerably in their function. The former Virus removal software work as a preventive measures, while the other one gives offensive approach.
Virus removal software are of different category. Let's get familiar with tested and certified list.
McAfee Family Protection
If you want to get comprehensive and economical PC security then don't waste your time. Get the 1-Year Subscription for 3PCs @ $39.99(USD). You will get the below commitment:
Ban objectionable Websites --Objectionable websites will get filtered so that you are safeguarded from obscene contents.
Decide correct YouTube Videos for kids--Unique key word filtering technology will allow only selected videos.
Schedule time table for kids online--You can schedule timetable for kids so that they don't make misuse of Internet.
Let your family enjoy instant messaging-- It will monitors and records instant message conversations and restrain you from improper dialogue or conversations with strangers.
Online Virus scan tools are too available which can scan and remove viruses on the spot so that you can enjoy healthy computer. These virus removal tools needs to be executed from suitable web browser.
Avira AntiVir Personal for Windows
Above online Virus removal tool provides an easy-to-use interface and pre-configured scan tasks. Hence it will quickly scan your most important drives and folders. You can perform scanning of individual files and folders with the right-click option in Explorer or on the desktop. Alternatively files can be dragged and dropped into the AntiVir virus removal console for quick scanning.
Avira AntiVir Personal online Virus removal tool can be used in Safe Mode. Hence a very effective if the window is not able to boot in normal mode.
Virus removal softwares are available in two modes, the first one is the independent or third party software and other is online scanner. Both differ considerably in their function. The former Virus removal software work as a preventive measures, while the other one gives offensive approach.
Virus removal software are of different category. Let's get familiar with tested and certified list.
McAfee Family Protection
If you want to get comprehensive and economical PC security then don't waste your time. Get the 1-Year Subscription for 3PCs @ $39.99(USD). You will get the below commitment:
Ban objectionable Websites --Objectionable websites will get filtered so that you are safeguarded from obscene contents.
Decide correct YouTube Videos for kids--Unique key word filtering technology will allow only selected videos.
Schedule time table for kids online--You can schedule timetable for kids so that they don't make misuse of Internet.
Let your family enjoy instant messaging-- It will monitors and records instant message conversations and restrain you from improper dialogue or conversations with strangers.
Online Virus scan tools are too available which can scan and remove viruses on the spot so that you can enjoy healthy computer. These virus removal tools needs to be executed from suitable web browser.
Avira AntiVir Personal for Windows
Above online Virus removal tool provides an easy-to-use interface and pre-configured scan tasks. Hence it will quickly scan your most important drives and folders. You can perform scanning of individual files and folders with the right-click option in Explorer or on the desktop. Alternatively files can be dragged and dropped into the AntiVir virus removal console for quick scanning.
Avira AntiVir Personal online Virus removal tool can be used in Safe Mode. Hence a very effective if the window is not able to boot in normal mode.
Etiquetas:
antivirus,
antivirus solution
Tape backup software
Tape backup softwareis another comprehensive backup software that can provide full or partial back up to your computer’s data. This backup software is relevant for both home and business users. Backup is so compressed and encrypted that it is safe against any vulnerable condition.
Let us know in briedstudy about some key tape backup software:
Atempo Live Backup
Atempo Live backup support provides real-time protection to your backup data. It will backup your data without any changes in the original documents. It is user-friendly and you can sit calmly once you started the backup wizard. It will auto-check so that no data is duplicated. In addition, if there is any obstructer in your system it will take care of it with its Management Console interface. It is also capable of restoring unbootable PCs without re-installation of the operating system. This backup software has immense storage capacity on account of zip compression and reluctant elimination technology.
Atempo digital archive
As we know, the e-mail has become the vital dose of our professional life. The growing e-mail communication puts extra loads on the server. Hence,to maintain them you can trust on Atempo digital archive. It helps the user to streamline mailbox management and enhance litigation.. End uses would be able to organize and search their e-mails in an effective manner.
In addition, ADAM is also capable tof satisfying the robust modules of electronic communication through pre-filtering, rapid retrieval, retention policy management, and electronic communications supervision.
Atempo time navigator
This is a unique Tape data backup software which can manage enterprise data throughout its life-cycle to meet critical business requirements. This is the best choice for enterprises due to unlimited scalability and unique restoration approach that is compatible to all levels of businesses. It can managebackup of multi-location enterprise network.
Let us know in briedstudy about some key tape backup software:
Atempo Live Backup
Atempo Live backup support provides real-time protection to your backup data. It will backup your data without any changes in the original documents. It is user-friendly and you can sit calmly once you started the backup wizard. It will auto-check so that no data is duplicated. In addition, if there is any obstructer in your system it will take care of it with its Management Console interface. It is also capable of restoring unbootable PCs without re-installation of the operating system. This backup software has immense storage capacity on account of zip compression and reluctant elimination technology.
Atempo digital archive
As we know, the e-mail has become the vital dose of our professional life. The growing e-mail communication puts extra loads on the server. Hence,to maintain them you can trust on Atempo digital archive. It helps the user to streamline mailbox management and enhance litigation.. End uses would be able to organize and search their e-mails in an effective manner.
In addition, ADAM is also capable tof satisfying the robust modules of electronic communication through pre-filtering, rapid retrieval, retention policy management, and electronic communications supervision.
Atempo time navigator
This is a unique Tape data backup software which can manage enterprise data throughout its life-cycle to meet critical business requirements. This is the best choice for enterprises due to unlimited scalability and unique restoration approach that is compatible to all levels of businesses. It can managebackup of multi-location enterprise network.
Etiquetas:
backup,
backup software
Best free backup software
Data stored on your system are of vital importance to you. They keep your valuable photos, giant music collection, important documents and other things safely. You may suffer data loss anytime. Hence, it is very important to keep regular data backup to handle any such situation. This is not going to cost anything to you. Thanks to the software developers who are working deliberately to keep your data secure. Now a days you have plenty of options among best free backup software.
Now let's make a survey of some important best free data backup support software.
Data loss is always costly and stressful. Hard drives always crashand with no prior information. Therefore is is important to DO regular backups. Especially, when there are so many free backup software options that can run regular backups automatically. Just set it once to run scheduled backups every week or so and forget about them. When disaster happens you will be able to restore your files in no time.
Comodo Backup
You can blindly trust on comodo Backup free backup software. It is user-friendly, easy to install and execute. It can create exact duplicate copy of the files and folders that needs to be backed up. You have the option to restore these data on any external hard drive, FTP server or any USB drive. In addition, this best free backup software is also equipped with features of synchronization, e-mail reporting, extensive history logs, advanced rule-based filtering;,encryption and password protection.
GFI BACKUP
This is the best free backup software for the average user. It can backup archives as zip files and encrypt them as per your choice. It can perform incremental and differential backups and restore data to multiple location.
Fbackup
Fbackup isone of the best among free data backup software. It is easy to execute with the help of wizard and it is compatible to the Backup4all plugins data backup software. Fbackup in association with the plugins can automatically backup data from a wide variety of different programs.
Now let's make a survey of some important best free data backup support software.
Data loss is always costly and stressful. Hard drives always crashand with no prior information. Therefore is is important to DO regular backups. Especially, when there are so many free backup software options that can run regular backups automatically. Just set it once to run scheduled backups every week or so and forget about them. When disaster happens you will be able to restore your files in no time.
Comodo Backup
You can blindly trust on comodo Backup free backup software. It is user-friendly, easy to install and execute. It can create exact duplicate copy of the files and folders that needs to be backed up. You have the option to restore these data on any external hard drive, FTP server or any USB drive. In addition, this best free backup software is also equipped with features of synchronization, e-mail reporting, extensive history logs, advanced rule-based filtering;,encryption and password protection.
GFI BACKUP
This is the best free backup software for the average user. It can backup archives as zip files and encrypt them as per your choice. It can perform incremental and differential backups and restore data to multiple location.
Fbackup
Fbackup isone of the best among free data backup software. It is easy to execute with the help of wizard and it is compatible to the Backup4all plugins data backup software. Fbackup in association with the plugins can automatically backup data from a wide variety of different programs.
Etiquetas:
backup
Microsoft windows upgrade
Soon after the launch of any latest version of Windows, Microsoft tries to get the users attracted to the new platform. But this is not an easy task because the users get addicted to the older one.They feel more comfortable with them. Hence, the promos of the company focuses on the key benefit of the latest one which replaces the older one. It doesn't left any stone unturned. In general term Windows upgrade means to get migrated to a latest windows operating system. It can be achieved in two different ways. The former one is custom installation and the later can be termed as clean installation.
With the launch of Windows 7 on 22 Oct '2009, Microsoft played its cards with Windows 7 Upgrade Option. It popularized the scheme in association with different computers and laptops manufacturer. Manufacturer were in turn also benefited, in the dual deal. The form of Microsoft Windows Upgrade are available with the manufacturer, the user needs to visit them and fill the form, or do it online. All the language and territory details needs to be fill in the form. After the form is accepted the user will get the DVDs of upgrade and a confirmation on their email.
Microsoft Windows Upgrade has its merits that you can retain in your files and settings of the previous versions. Also this upgrade will be easier for you. Just insert the Windows 7 upgrade software into your PC's DVD drive and follow the instructions on your screen.
In case you are not eligible then you need to check your system with Windows 7 Upgrade Advisor. It will scan your PC and tell whether the upgrade is possible? If not, then it will suggest about the hardware configuration. Follow them and get installed Windows 7.
With the launch of Windows 7 on 22 Oct '2009, Microsoft played its cards with Windows 7 Upgrade Option. It popularized the scheme in association with different computers and laptops manufacturer. Manufacturer were in turn also benefited, in the dual deal. The form of Microsoft Windows Upgrade are available with the manufacturer, the user needs to visit them and fill the form, or do it online. All the language and territory details needs to be fill in the form. After the form is accepted the user will get the DVDs of upgrade and a confirmation on their email.
Microsoft Windows Upgrade has its merits that you can retain in your files and settings of the previous versions. Also this upgrade will be easier for you. Just insert the Windows 7 upgrade software into your PC's DVD drive and follow the instructions on your screen.
In case you are not eligible then you need to check your system with Windows 7 Upgrade Advisor. It will scan your PC and tell whether the upgrade is possible? If not, then it will suggest about the hardware configuration. Follow them and get installed Windows 7.
Etiquetas:
upgrade windows,
windows
Online Virus Scan - iYogi UK
Online virus scan is an effective tool against virus. This tool can be downloaded from the web browser and after execution it will ensure100 percent removal from all kinds of viruses, worms, trojans, and all kinds of malware detected by powerful scan engines. This doesn't ensure permanent protection. For that, you need to take help of independent anti-virus software and install antivirus.
Let's get familiarize with some important online virus scanner.
VirusChief:
VirusChief, Online virus scan is not going to replace any antivirus software installed on your PC. It scans individual files on demand only. It offers superior detection rate, but it may harm other files( In rare cases) too. Just enter the file on the browser you want to scan and it will execute the response in just a minute. Best for the average users.
Virustotal:
VirusTotal, Online virus scan has been awarded by the American edition of PC World Magazine. It analyzes suspicious files and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware without any delay. Its scanning is far superior than any antivirus engines. As it does real-time updates of virus signature hence more effectual to provide quick removal.
Important: If a user is present in a remote location he can generate e-mails and attach the required files to get delivered to online virus scan for diagnosis. However, the attachment should not exceed 20 MB file size.
At the end, the user will get a detailled report, which will show the statistics of the infected part. It will show the success and failure of online virus scan in terms of bar graph.
Let's get familiarize with some important online virus scanner.
VirusChief:
VirusChief, Online virus scan is not going to replace any antivirus software installed on your PC. It scans individual files on demand only. It offers superior detection rate, but it may harm other files( In rare cases) too. Just enter the file on the browser you want to scan and it will execute the response in just a minute. Best for the average users.
Virustotal:
VirusTotal, Online virus scan has been awarded by the American edition of PC World Magazine. It analyzes suspicious files and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware without any delay. Its scanning is far superior than any antivirus engines. As it does real-time updates of virus signature hence more effectual to provide quick removal.
Important: If a user is present in a remote location he can generate e-mails and attach the required files to get delivered to online virus scan for diagnosis. However, the attachment should not exceed 20 MB file size.
At the end, the user will get a detailled report, which will show the statistics of the infected part. It will show the success and failure of online virus scan in terms of bar graph.
Etiquetas:
antivirus
Nod32 vs Avira vs Kaspersky
Hola Buenas pues tras un mes de investigaciones entre estos 3 Antivirus llege a una conclusion el kaspersky es muy superior a estos 2 antivirus !!
Pues bueno mis pruebas fueron las siguientes con todos los campos de los Antivirus y destacar la heristicas de Avira Antivir en encritaciones pero destacar su gran destresesa para los Falsos positivos ya que tiene muxisimos!!
TAN SOLO ES MI OPINION CON LAS PRUEBAS QUE ICE !!
Kaspersky: motor heristico: 2 (Se esta mejorando)
Firewall: 9.90
Defensa Preventiva: 10 (lee todo tipos de encritaciones movimientos ect)
(Imposible de pasar nos avisa de todo tan solo el problemas de los .bat que kaspersky esta trabajanso en ello ) (modo de que salte)(NO EN AUTOMATICO)
Avira Antivir: Motor heristico encrtitaciones 9 (Facil de burlar con un encritador polimorfico )
Firewall: 5
Nord32: Heristica 6
firewall: 5
Sorprendetemen el nod32 me dececiono del todo aki la aclaracion con una de las pruebas:
Coded in delpi
Coded by x-zer0
Stub size - 16kb
Probado con Bifrost
Antivirus Versione Ultimo aggiornamento Risultato
AhnLab-V3 2008.7.8.0 2008.07.07 -
AntiVir 7.8.0.64 2008.07.07 BDS/Poison.CPD
Authentium 5.1.0.4 2008.07.07 -
Avast 4.8.1195.0 2008.07.07 Win32oison-DE
AVG 7.5.0.516 2008.07.07 Dropper.Delf
BitDefender 7.2 2008.07.08 Trojan.Downloader.Agent.ZCR
CAT-QuickHeal 9.50 2008.07.07 (Suspicious) - DNAScan
ClamAV 0.93.1 2008.07.08 Trojan.Downloader-24465
DrWeb 4.44.0.09170 2008.07.07 -
eSafe 7.0.17.0 2008.07.07 Suspicious File
eTrust-Vet 31.6.5934 2008.07.07 -
Ewido 4.0 2008.07.07 Not-A-Virus.Constructor.Win32.MicroJoiner.17
F-Prot 4.4.4.56 2008.07.07 W32/DelfInject.A.gen!Eldorado
F-Secure 7.60.13501.0 2008.07.08 W32/Malware
Fortinet 3.14.0.0 2008.07.07 -
GData 2.0.7306.1023 2008.07.08 Win32oison-DE
Ikarus T3.1.1.26.0 2008.07.08 Backdoor.Win32.PoisonIvy.ay
Kaspersky 7.0.0.125 2008.07.08 Heur.Trojan.Generic
McAfee 5333 2008.07.07 -
Microsoft 1.3704 2008.07.08 VirTool:Win32/DelfInject.gen!X
NOD32v2 3248 2008.07.07 -
Norman 5.80.02 2008.07.07 W32/Malware
Panda 9.0.0.4 2008.07.08 Suspicious file
Prevx1 V2 2008.07.08 -
Rising 20.51.60.00 2008.07.06 -
Sophos 4.31.0 2008.07.07 Mal/Mdrop-E
Sunbelt 3.1.1509.1 2008.07.04 -
Symantec 10 2008.07.08 Backdoor.Trojan
TheHacker 6.2.96.374 2008.07.07 -
TrendMicro 8.700.0.1004 2008.07.07 -
VBA32 3.12.6.8 2008.07.07 suspected of Trojan-PSW.Pinch.90 (paranoid heuristics)
VirusBuster 4.5.11.0 2008.07.07 -
Webwasher-Gateway 6.6.2 2008.07.07 Trojan.Backdoor.Poison.CPD
Informazioni addizionali
File size: 22528 bytes
MD5...: 5242a0adbb38b1039ae1abda70979007
SHA1..: b57f67ffbb56c7393b3ec9a59e506a88de7b09e5
SHA256: bdddfef13cece17c2ed77ae2b340729c34b5bb21761c27864bff23c6f7ae98bc
SHA512: e36d2b206b8392c38a4878cecc8083249d28ec20543d5e2a6ec0e52a88bb0f88
54e3a9dcabb55a47908c114e1923880b7521189dc58e0b3635689514306f7a19
PEiD..: -
nord32 no es capas de leer el encritamiento de este encritador y encima su firewall deja pasar el bifrost gracias ala encritacion eso suele ocurrir en Antivirus que se basan solo en su heuristica como nord32 y Avira Antivir si burlamos su heuristica conseguimos burlar al antivirus en el 90% de los casos
Aki un ejemplo de Avira antivir burlando su heurisitica con un encritador:
AhnLab-V3 2008.5.10.0 2008.05.13 -
AntiVir 7.8.0.17 2008.05.13 -
Authentium 5.1.0.4 2008.05.13 -
Avast 4.8.1195.0 2008.05.13 -
AVG 7.5.0.516 2008.05.13 BackDoor.Generic9.ALRK
BitDefender 7.2 2008.05.08 Trojan.VB.NRC
CAT-QuickHeal 9.50 2008.05.13 -
ClamAV 0.92.1 2008.05.13 -
DrWeb 4.44.0.09170 2008.05.13 -
eSafe 7.0.15.0 2008.05.13 -
eTrust-Vet 31.4.5783 2008.05.12 -
Ewido 4.0 2008.05.13 -
F-Prot 4.4.2.54 2008.05.13 -
F-Secure 6.70.13260.0 2008.05.13 -
Fortinet 3.14.0.0 2008.05.13 -
GData 2.0.7306.1023 2008.05.13 -
Ikarus T3.1.1.26.0 2008.05.13 Virus.Trojan.Win32.Buzus.gdl
Kaspersky 7.0.0.125 2008.05.13 -
McAfee 5294 2008.05.13 -
Microsoft 1.3520 2008.05.13 Trojan:Win32/VB.ZK
NOD32v2 3096 2008.05.13 -
Norman 5.80.02 2008.05.13 -
Panda 9.0.0.4 2008.05.12 -
Prevx1 V2 2008.05.13 -
Rising 20.44.12.00 2008.05.13 -
Sophos 4.29.0 2008.05.13 Mal/Behav-103
Sunbelt 3.0.1114.0 2008.05.12 -
Symantec 10 2008.05.13 -
TheHacker 6.2.92.309 2008.05.13 -
VBA32 3.12.6.6 2008.05.13 Trojan.Win32.Buzus.gdl
VirusBuster 4.3.26:9 2008.05.13 -
Webwasher-Gateway 6.6.2 2008.05.13 -
Motor antivirus Versión Última actualización Resultado
AhnLab-V3 2008.5.3.0 2008.05.07 -
AntiVir 7.8.0.11 2008.05.07 -
Authentium 4.93.8 2008.05.07 -
Avast 4.8.1169.0 2008.05.06 -
AVG 7.5.0.516 2008.05.07 BackDoor.Generic9.ALRK
BitDefender 7.2 2008.05.07 -
CAT-QuickHeal 9.50 2008.05.06 -
ClamAV 0.92.1 2008.05.07 -
DrWeb 4.44.0.09170 2008.05.07 -
eSafe 7.0.15.0 2008.05.06 -
eTrust-Vet 31.4.5766 2008.05.07 -
Ewido 4.0 2008.05.06 -
F-Prot 4.4.2.54 2008.05.06 -
F-Secure 6.70.13260.0 2008.05.07 -
Fortinet 3.14.0.0 2008.05.07 -
Ikarus T3.1.1.26.0 2008.05.07 -
Kaspersky 7.0.0.125 2008.05.07 -
McAfee 5289 2008.05.06 -
Microsoft 1.3408 2008.05.07 -
NOD32v2 3082 2008.05.07 -
Norman 5.80.02 2008.05.06 -
Panda 9.0.0.4 2008.05.06 -
Rising 20.43.12.00 2008.05.07 -
Sophos 4.29.0 2008.05.07 -
Sunbelt 3.0.1097.0 2008.05.07 -
Symantec 10 2008.05.07 -
TheHacker 6.2.92.302 2008.05.07 -
VBA32 3.12.6.5 2008.05.06 -
VirusBuster 4.3.26:9 2008.05.06 -
Webwasher-Gateway 6.6.2 2008.05.07 -
Conclusion de todo me quedo con kaspersky superios en muxos de los aspectos y para los hacker el antivirus mas dificil de burlar (hasta dia de hoy no se conoce nadie que haya podido burlar la defensa preventiva de kaspersky con el control de registro activado )
PD: Esperemos a Septiembre aver que nos tiene preparado kaspersky !! (supuestamente tendremos nuestro modulo contra los .bat y todos los fallos reportados solucioneados)
Esto es solo una prueba, a cada uno un antivirus le puede funcionar bien o no.
por ejemplo amii el nod32, no me parecio bueno, no me eliminaba mucho, pero a otros es le funciono ii es genial. Yo creo que depende de suerte, jeje
Pues bueno mis pruebas fueron las siguientes con todos los campos de los Antivirus y destacar la heristicas de Avira Antivir en encritaciones pero destacar su gran destresesa para los Falsos positivos ya que tiene muxisimos!!
TAN SOLO ES MI OPINION CON LAS PRUEBAS QUE ICE !!
Kaspersky: motor heristico: 2 (Se esta mejorando)
Firewall: 9.90
Defensa Preventiva: 10 (lee todo tipos de encritaciones movimientos ect)
(Imposible de pasar nos avisa de todo tan solo el problemas de los .bat que kaspersky esta trabajanso en ello ) (modo de que salte)(NO EN AUTOMATICO)
Avira Antivir: Motor heristico encrtitaciones 9 (Facil de burlar con un encritador polimorfico )
Firewall: 5
Nord32: Heristica 6
firewall: 5
Sorprendetemen el nod32 me dececiono del todo aki la aclaracion con una de las pruebas:
Coded in delpi
Coded by x-zer0
Stub size - 16kb
Probado con Bifrost
Antivirus Versione Ultimo aggiornamento Risultato
AhnLab-V3 2008.7.8.0 2008.07.07 -
AntiVir 7.8.0.64 2008.07.07 BDS/Poison.CPD
Authentium 5.1.0.4 2008.07.07 -
Avast 4.8.1195.0 2008.07.07 Win32oison-DE
AVG 7.5.0.516 2008.07.07 Dropper.Delf
BitDefender 7.2 2008.07.08 Trojan.Downloader.Agent.ZCR
CAT-QuickHeal 9.50 2008.07.07 (Suspicious) - DNAScan
ClamAV 0.93.1 2008.07.08 Trojan.Downloader-24465
DrWeb 4.44.0.09170 2008.07.07 -
eSafe 7.0.17.0 2008.07.07 Suspicious File
eTrust-Vet 31.6.5934 2008.07.07 -
Ewido 4.0 2008.07.07 Not-A-Virus.Constructor.Win32.MicroJoiner.17
F-Prot 4.4.4.56 2008.07.07 W32/DelfInject.A.gen!Eldorado
F-Secure 7.60.13501.0 2008.07.08 W32/Malware
Fortinet 3.14.0.0 2008.07.07 -
GData 2.0.7306.1023 2008.07.08 Win32oison-DE
Ikarus T3.1.1.26.0 2008.07.08 Backdoor.Win32.PoisonIvy.ay
Kaspersky 7.0.0.125 2008.07.08 Heur.Trojan.Generic
McAfee 5333 2008.07.07 -
Microsoft 1.3704 2008.07.08 VirTool:Win32/DelfInject.gen!X
NOD32v2 3248 2008.07.07 -
Norman 5.80.02 2008.07.07 W32/Malware
Panda 9.0.0.4 2008.07.08 Suspicious file
Prevx1 V2 2008.07.08 -
Rising 20.51.60.00 2008.07.06 -
Sophos 4.31.0 2008.07.07 Mal/Mdrop-E
Sunbelt 3.1.1509.1 2008.07.04 -
Symantec 10 2008.07.08 Backdoor.Trojan
TheHacker 6.2.96.374 2008.07.07 -
TrendMicro 8.700.0.1004 2008.07.07 -
VBA32 3.12.6.8 2008.07.07 suspected of Trojan-PSW.Pinch.90 (paranoid heuristics)
VirusBuster 4.5.11.0 2008.07.07 -
Webwasher-Gateway 6.6.2 2008.07.07 Trojan.Backdoor.Poison.CPD
Informazioni addizionali
File size: 22528 bytes
MD5...: 5242a0adbb38b1039ae1abda70979007
SHA1..: b57f67ffbb56c7393b3ec9a59e506a88de7b09e5
SHA256: bdddfef13cece17c2ed77ae2b340729c34b5bb21761c27864bff23c6f7ae98bc
SHA512: e36d2b206b8392c38a4878cecc8083249d28ec20543d5e2a6ec0e52a88bb0f88
54e3a9dcabb55a47908c114e1923880b7521189dc58e0b3635689514306f7a19
PEiD..: -
nord32 no es capas de leer el encritamiento de este encritador y encima su firewall deja pasar el bifrost gracias ala encritacion eso suele ocurrir en Antivirus que se basan solo en su heuristica como nord32 y Avira Antivir si burlamos su heuristica conseguimos burlar al antivirus en el 90% de los casos
Aki un ejemplo de Avira antivir burlando su heurisitica con un encritador:
AhnLab-V3 2008.5.10.0 2008.05.13 -
AntiVir 7.8.0.17 2008.05.13 -
Authentium 5.1.0.4 2008.05.13 -
Avast 4.8.1195.0 2008.05.13 -
AVG 7.5.0.516 2008.05.13 BackDoor.Generic9.ALRK
BitDefender 7.2 2008.05.08 Trojan.VB.NRC
CAT-QuickHeal 9.50 2008.05.13 -
ClamAV 0.92.1 2008.05.13 -
DrWeb 4.44.0.09170 2008.05.13 -
eSafe 7.0.15.0 2008.05.13 -
eTrust-Vet 31.4.5783 2008.05.12 -
Ewido 4.0 2008.05.13 -
F-Prot 4.4.2.54 2008.05.13 -
F-Secure 6.70.13260.0 2008.05.13 -
Fortinet 3.14.0.0 2008.05.13 -
GData 2.0.7306.1023 2008.05.13 -
Ikarus T3.1.1.26.0 2008.05.13 Virus.Trojan.Win32.Buzus.gdl
Kaspersky 7.0.0.125 2008.05.13 -
McAfee 5294 2008.05.13 -
Microsoft 1.3520 2008.05.13 Trojan:Win32/VB.ZK
NOD32v2 3096 2008.05.13 -
Norman 5.80.02 2008.05.13 -
Panda 9.0.0.4 2008.05.12 -
Prevx1 V2 2008.05.13 -
Rising 20.44.12.00 2008.05.13 -
Sophos 4.29.0 2008.05.13 Mal/Behav-103
Sunbelt 3.0.1114.0 2008.05.12 -
Symantec 10 2008.05.13 -
TheHacker 6.2.92.309 2008.05.13 -
VBA32 3.12.6.6 2008.05.13 Trojan.Win32.Buzus.gdl
VirusBuster 4.3.26:9 2008.05.13 -
Webwasher-Gateway 6.6.2 2008.05.13 -
Motor antivirus Versión Última actualización Resultado
AhnLab-V3 2008.5.3.0 2008.05.07 -
AntiVir 7.8.0.11 2008.05.07 -
Authentium 4.93.8 2008.05.07 -
Avast 4.8.1169.0 2008.05.06 -
AVG 7.5.0.516 2008.05.07 BackDoor.Generic9.ALRK
BitDefender 7.2 2008.05.07 -
CAT-QuickHeal 9.50 2008.05.06 -
ClamAV 0.92.1 2008.05.07 -
DrWeb 4.44.0.09170 2008.05.07 -
eSafe 7.0.15.0 2008.05.06 -
eTrust-Vet 31.4.5766 2008.05.07 -
Ewido 4.0 2008.05.06 -
F-Prot 4.4.2.54 2008.05.06 -
F-Secure 6.70.13260.0 2008.05.07 -
Fortinet 3.14.0.0 2008.05.07 -
Ikarus T3.1.1.26.0 2008.05.07 -
Kaspersky 7.0.0.125 2008.05.07 -
McAfee 5289 2008.05.06 -
Microsoft 1.3408 2008.05.07 -
NOD32v2 3082 2008.05.07 -
Norman 5.80.02 2008.05.06 -
Panda 9.0.0.4 2008.05.06 -
Rising 20.43.12.00 2008.05.07 -
Sophos 4.29.0 2008.05.07 -
Sunbelt 3.0.1097.0 2008.05.07 -
Symantec 10 2008.05.07 -
TheHacker 6.2.92.302 2008.05.07 -
VBA32 3.12.6.5 2008.05.06 -
VirusBuster 4.3.26:9 2008.05.06 -
Webwasher-Gateway 6.6.2 2008.05.07 -
Conclusion de todo me quedo con kaspersky superios en muxos de los aspectos y para los hacker el antivirus mas dificil de burlar (hasta dia de hoy no se conoce nadie que haya podido burlar la defensa preventiva de kaspersky con el control de registro activado )
PD: Esperemos a Septiembre aver que nos tiene preparado kaspersky !! (supuestamente tendremos nuestro modulo contra los .bat y todos los fallos reportados solucioneados)
Esto es solo una prueba, a cada uno un antivirus le puede funcionar bien o no.
por ejemplo amii el nod32, no me parecio bueno, no me eliminaba mucho, pero a otros es le funciono ii es genial. Yo creo que depende de suerte, jeje
Etiquetas:
antivirus
ESET NOD32 vs Avira Security Suite vs Kaspersky Internet 200
Basicamente me dia ala tarea de realizar un analisis exasutivo de varios antivirus en este caso, los que desmotrasron mayor puntuacion en diferentes tests de seguridad, desde el prestigiado eset, hasta el aleman avira muy reciente pero muy potente, ademas con las innovaciones de KIS Y NIS 2009.
Comenzando con Avira Premium security suite:
+ Proteccion contra virus gusanos y troyanos
+ proteccion contra spy/adware
+ proteccion contra virus email POP3 SMTP
+ Proteccion contra pishing
+ proteccion contra pishing proactiva
+ monitor en tiempo real
+ antidrive (proteccion descarga malware)
+ CD rescue system (rescate de pc infectada)
+ webguard
+ antispam
+ firewall
+ backupsystem (guarda datos)
+ antibot
+ gamemode
version 8.1.0.245 (Ingles unicamente)
http://dlpe.antivir.com/down/windows/prem_sec_winnt_en_hp.exe
Eset nod32 smart security
+ proteccion contra virus gusanos y troyanos
+ proteccion contra spy/adware
+ proteccion contra malware
+ proteccion contra pishing en bandeja de correo
+ proteccion contra rootkits
+ monitor en tiempo real con threatSense
+ monitor de trafico de internet (http)
+ monitor de documentos de microsoft officce( yo no lo he visto jamas)
+ antispam
+ firewall bidireccional
+ consumo de pocos recursos
3.0.669 (español)
http://www.eset.eu/ess-download/ess_nt32_esn
Kaspersky Internet security 2009
+ proteccion contra virus gusanos y troyanos
+ proteccion correo pop3, smtp
+ proteccion de trafico de internet
+ proteccion msn, icq,
+ proteccion proactiva contra soft malicioso
+ analisis de java y visual basic
+ firewall
+ proteccion para redes
+ proteccion en equipos infectados
+ proteccion antipishing, antikeyloggers
+ proteccion de dialers
+ bloqueo de banners
+ creacion de discos de recuperacion
version 8.0.0.454 español
http://dnl-pr1.kaspersky-labs.com/products/spanish/homeuser/kis2009/kis8.0.0.454es.exe
Norton Internet Security 2009
+ proteccion virus
+ Protección contra software espía
+ Firewall bidireccional
+ Protección de la identidad
+ arranca y repara equipos infectados
+ Antiphishing
+ Supervisión de la red
+ Protección contra bots
+ Detección de rootkits
+ Protección del navegador
+ Protección contra gusanos de Internet
+ Prevención de intrusiones
+ Protección de aplicaciones y SO
+ Autenticación de sitios web
+ Actualizaciones rápidas
+ Norton™ Insight (analisis cortos rapidos, analisis de peligros)
+ Norton protection system ( defensa proactiva
+ Protección basada en comportamiento SONAR™
+ Antispam
+ Controles para padres y bloqueo de información confidencial
Norton Internet security 2009
http://spftrl.digitalriver.com/pub/symantec/tbyb/NAM/NIS09ES.exe
En lo personal quiero hacer notar
mis experiencias propias con los antivirus anteriores
Antivir ningun comentario, no me ha fallado
Eset nod32, me defraudo 2 veces, muy pobre la proteccion frente al malware, tube ke desinfectar mi pc con antivirus online como el etrust, panda online., muy funcional gracias al nodlogin
Kaspersky, creo que consumo mas recursos que cualkiera de los ke menciono, se me bloqueo la maquina 2 veces en el primer dia de instalacion, muy latoso estar cambiando las keys.
Norton 2009, en lo personal creo que lo mejoraron bastante, no le encontre defectos, solo que no encontre una licencia para seguir usandolo, muy escaso el crack esta recien salidito
Ojala les guste mi nota, ya que gual ke muchos de ustedes, dude en cual antivirus es mejor, y pues probe uno por uno por separado, por diferentes periodos, en lo personal me kedo con avira o con norton.
cabe aclarar que todo lo analisado fueron las suites de internet security. home or office edition. espeficidadas e la seccion de inicio
Comenzando con Avira Premium security suite:
+ Proteccion contra virus gusanos y troyanos
+ proteccion contra spy/adware
+ proteccion contra virus email POP3 SMTP
+ Proteccion contra pishing
+ proteccion contra pishing proactiva
+ monitor en tiempo real
+ antidrive (proteccion descarga malware)
+ CD rescue system (rescate de pc infectada)
+ webguard
+ antispam
+ firewall
+ backupsystem (guarda datos)
+ antibot
+ gamemode
version 8.1.0.245 (Ingles unicamente)
http://dlpe.antivir.com/down/windows/prem_sec_winnt_en_hp.exe
Eset nod32 smart security
+ proteccion contra virus gusanos y troyanos
+ proteccion contra spy/adware
+ proteccion contra malware
+ proteccion contra pishing en bandeja de correo
+ proteccion contra rootkits
+ monitor en tiempo real con threatSense
+ monitor de trafico de internet (http)
+ monitor de documentos de microsoft officce( yo no lo he visto jamas)
+ antispam
+ firewall bidireccional
+ consumo de pocos recursos
3.0.669 (español)
http://www.eset.eu/ess-download/ess_nt32_esn
Kaspersky Internet security 2009
+ proteccion contra virus gusanos y troyanos
+ proteccion correo pop3, smtp
+ proteccion de trafico de internet
+ proteccion msn, icq,
+ proteccion proactiva contra soft malicioso
+ analisis de java y visual basic
+ firewall
+ proteccion para redes
+ proteccion en equipos infectados
+ proteccion antipishing, antikeyloggers
+ proteccion de dialers
+ bloqueo de banners
+ creacion de discos de recuperacion
version 8.0.0.454 español
http://dnl-pr1.kaspersky-labs.com/products/spanish/homeuser/kis2009/kis8.0.0.454es.exe
Norton Internet Security 2009
+ proteccion virus
+ Protección contra software espía
+ Firewall bidireccional
+ Protección de la identidad
+ arranca y repara equipos infectados
+ Antiphishing
+ Supervisión de la red
+ Protección contra bots
+ Detección de rootkits
+ Protección del navegador
+ Protección contra gusanos de Internet
+ Prevención de intrusiones
+ Protección de aplicaciones y SO
+ Autenticación de sitios web
+ Actualizaciones rápidas
+ Norton™ Insight (analisis cortos rapidos, analisis de peligros)
+ Norton protection system ( defensa proactiva
+ Protección basada en comportamiento SONAR™
+ Antispam
+ Controles para padres y bloqueo de información confidencial
Norton Internet security 2009
http://spftrl.digitalriver.com/pub/symantec/tbyb/NAM/NIS09ES.exe
En lo personal quiero hacer notar
mis experiencias propias con los antivirus anteriores
Antivir ningun comentario, no me ha fallado
Eset nod32, me defraudo 2 veces, muy pobre la proteccion frente al malware, tube ke desinfectar mi pc con antivirus online como el etrust, panda online., muy funcional gracias al nodlogin
Kaspersky, creo que consumo mas recursos que cualkiera de los ke menciono, se me bloqueo la maquina 2 veces en el primer dia de instalacion, muy latoso estar cambiando las keys.
Norton 2009, en lo personal creo que lo mejoraron bastante, no le encontre defectos, solo que no encontre una licencia para seguir usandolo, muy escaso el crack esta recien salidito
Ojala les guste mi nota, ya que gual ke muchos de ustedes, dude en cual antivirus es mejor, y pues probe uno por uno por separado, por diferentes periodos, en lo personal me kedo con avira o con norton.
cabe aclarar que todo lo analisado fueron las suites de internet security. home or office edition. espeficidadas e la seccion de inicio
Etiquetas:
antivirus
sábado, 12 de diciembre de 2009
Instructions for Installing MySQL on Windows
Download MySQL v5.1
Download MySQL from http://dev.mysql.com/downloads/mysql/5.1.html Just make sure you get a Windows Essentials (x86) binary version. (after you click the "pick a mirror," if it asks you to login, scroll down a little and click the "No thanks, just take me to the downloads!" link under the login form)
My file was named: mysql-essential-5.1.33-win32.msi
Install MySQL v5.1
Run the MSI file and use the following settings
Typical Setup
Skip Sign-Up
make sure "Configure the MySQL Server now" is checked
"Detailed Configuration"
"Developer Machine"
"Multifunctional Database"
"InnoDB Tablespace Settings" - leave everything default
"Decision Support (DSS)/OLAP"
make sure "Enable TCP/IP Networking" is checked and leave the port number at 3306 (at this point, if you have a firewall, it will usually try to access itself on the localhost)
Leave "Enable Strict Mode" checked
"Standard Character Set"
check "Install As Windows Service" and I would recommend leaving "Launch the MySQL Server automatically" checked.
enter your root password and I would recommend leaving "Enable root access from remote machines" unchecked
then hit "execute" and it'll install and set it up.
Getting PHP5 to work with MySQL - Official Info
Unfortunately PHP5 removed built-in support for MySQL. To get it to work, the easiest way is to copy the mysql library file by hand. Open the folder you unzipped your PHP to. Copy the libmysql.dll file (should be located like C:\php\libmysql.dll ) into your Window's System folder (usually C:\Windows\System32\ although might be C:\WinNT\System\ or something).
Then open up your php.ini in a text editor and search for ;extension=php_mysql.dll and remove the ; infont of that line.
Restart Apache and see if you get any errors. If it complains about "php_mysql.dll" either your extension directory isn't correct or windows can't find libmysql.dll
Testing MySQL
Testing MySQL is not exactly easy. However, here are the common connection strings for PHP. I recommend downloading phpMyAdmin and using it to create and manage your databases, etc.
PHP Connection test
";
mysql_select_db("$dbName") or die("Could not select database");
print "Database selected successfully
";
// close connection
mysql_close($link);
?>
Download MySQL from http://dev.mysql.com/downloads/mysql/5.1.html Just make sure you get a Windows Essentials (x86) binary version. (after you click the "pick a mirror," if it asks you to login, scroll down a little and click the "No thanks, just take me to the downloads!" link under the login form)
My file was named: mysql-essential-5.1.33-win32.msi
Install MySQL v5.1
Run the MSI file and use the following settings
Typical Setup
Skip Sign-Up
make sure "Configure the MySQL Server now" is checked
"Detailed Configuration"
"Developer Machine"
"Multifunctional Database"
"InnoDB Tablespace Settings" - leave everything default
"Decision Support (DSS)/OLAP"
make sure "Enable TCP/IP Networking" is checked and leave the port number at 3306 (at this point, if you have a firewall, it will usually try to access itself on the localhost)
Leave "Enable Strict Mode" checked
"Standard Character Set"
check "Install As Windows Service" and I would recommend leaving "Launch the MySQL Server automatically" checked.
enter your root password and I would recommend leaving "Enable root access from remote machines" unchecked
then hit "execute" and it'll install and set it up.
Getting PHP5 to work with MySQL - Official Info
Unfortunately PHP5 removed built-in support for MySQL. To get it to work, the easiest way is to copy the mysql library file by hand. Open the folder you unzipped your PHP to. Copy the libmysql.dll file (should be located like C:\php\libmysql.dll ) into your Window's System folder (usually C:\Windows\System32\ although might be C:\WinNT\System\ or something).
Then open up your php.ini in a text editor and search for ;extension=php_mysql.dll and remove the ; infont of that line.
Restart Apache and see if you get any errors. If it complains about "php_mysql.dll" either your extension directory isn't correct or windows can't find libmysql.dll
Testing MySQL
Testing MySQL is not exactly easy. However, here are the common connection strings for PHP. I recommend downloading phpMyAdmin and using it to create and manage your databases, etc.
PHP Connection test
";
mysql_select_db("$dbName") or die("Could not select database");
print "Database selected successfully
";
// close connection
mysql_close($link);
?>
Etiquetas:
database server,
installing mysql,
mysql,
mysql server,
mysql xp
How to install Java
What is Java and why do I need it?
Java is a programming language that allows programs to be written that can then be run on more than one type of operating system. A program written in Java can run on Windows, UNIX, Linux etc. as long as there is a Java runtime environment installed.
Some of the programs on this website have been written in Java, so you will need to install the Java runtime environment in order to run them.
Where can I download Java?
You can download version 1.4 of Java from http://java.sun.com/j2se/1.4/download.html. If you want to be able to write your own Java programs that you can compile and run, then you must download the SDK (Software Developers Kit). If you just want to be able to run a Java program that has already been compiled, then you can get away with just downloading the JRE (Java Runtime Environment). Once you have decided which you need, download either the SDK or the JRE. Choose the download that is most suitable for your operating system.
Setting up Java
If you do not have Java installed already, follow the instructions provided with the download in order to install Java.
Once Java has been installed, you will be able to run Java program by running the java executable that was installed. You may find it convenient to add the location of this file to your operating system's path variable, otherwise you will need to explicitly refer to the absolute location of java.
Setting up the path
Windows 2000/XP users may set their path by right-clicking on 'My Computer' and selecting 'Properties'. Under the 'Advanced' tab, there is a button that allows you to set the 'Environment variables'. Click on this and alter the 'Path' variable so that it also contains the path to the Java executable. For example, if you have installed Java in c:\jdk and your path is currently set to C:\WINDOWS\SYSTEM32, then you would change your path to read C:\WINDOWS\SYSTEM32;c:\jdk\bin
When you open a new command prompt, it will reflect these changes and allow you to run java programs by typing "java". If you have installed the SDK, then you will also be able to run "javac" to compile stuff.
Windows 95/98/ME users may find that their path variable is stored in a different place. Edit the c:\autoexec.bat file and add the following line at the end: SET PATH=%PATH%;c:\jdk\bin
(This also assumes that you have installed Java in c:\jdk)
Linux, UNIX, Solaris, FreeBSD users must set their PATH variable to point to where the java binaries have been installed. Please refer to your shell documentation if you have trouble doing this. For example, if you use bash as your shell, then you would add the following line to the end of your .bashrc: export PATH=/path/to/java:$PATH
Setting up the classpath
In addition to setting up the path, you also need to tell Java where to find compiled class files at runtime. You will probably want to set the classpath to include at least the current working directory (.)
Eg: SET CLASSPATH=%CLASSPATH%;.
The classpath can also contain other directories that may contain compiled class files. Note that if you are using classes that are contained inside a .jar file, you will need to specify the full path and name of this file in the classpath, rather than just the name of the directory it is contained within.
Java Documentation
You may optionally download the Java documentation, which includes API pages that explain in good detail how each Java class can be used.
Java is a programming language that allows programs to be written that can then be run on more than one type of operating system. A program written in Java can run on Windows, UNIX, Linux etc. as long as there is a Java runtime environment installed.
Some of the programs on this website have been written in Java, so you will need to install the Java runtime environment in order to run them.
Where can I download Java?
You can download version 1.4 of Java from http://java.sun.com/j2se/1.4/download.html. If you want to be able to write your own Java programs that you can compile and run, then you must download the SDK (Software Developers Kit). If you just want to be able to run a Java program that has already been compiled, then you can get away with just downloading the JRE (Java Runtime Environment). Once you have decided which you need, download either the SDK or the JRE. Choose the download that is most suitable for your operating system.
Setting up Java
If you do not have Java installed already, follow the instructions provided with the download in order to install Java.
Once Java has been installed, you will be able to run Java program by running the java executable that was installed. You may find it convenient to add the location of this file to your operating system's path variable, otherwise you will need to explicitly refer to the absolute location of java.
Setting up the path
Windows 2000/XP users may set their path by right-clicking on 'My Computer' and selecting 'Properties'. Under the 'Advanced' tab, there is a button that allows you to set the 'Environment variables'. Click on this and alter the 'Path' variable so that it also contains the path to the Java executable. For example, if you have installed Java in c:\jdk and your path is currently set to C:\WINDOWS\SYSTEM32, then you would change your path to read C:\WINDOWS\SYSTEM32;c:\jdk\bin
When you open a new command prompt, it will reflect these changes and allow you to run java programs by typing "java". If you have installed the SDK, then you will also be able to run "javac" to compile stuff.
Windows 95/98/ME users may find that their path variable is stored in a different place. Edit the c:\autoexec.bat file and add the following line at the end: SET PATH=%PATH%;c:\jdk\bin
(This also assumes that you have installed Java in c:\jdk)
Linux, UNIX, Solaris, FreeBSD users must set their PATH variable to point to where the java binaries have been installed. Please refer to your shell documentation if you have trouble doing this. For example, if you use bash as your shell, then you would add the following line to the end of your .bashrc: export PATH=/path/to/java:$PATH
Setting up the classpath
In addition to setting up the path, you also need to tell Java where to find compiled class files at runtime. You will probably want to set the classpath to include at least the current working directory (.)
Eg: SET CLASSPATH=%CLASSPATH%;.
The classpath can also contain other directories that may contain compiled class files. Note that if you are using classes that are contained inside a .jar file, you will need to specify the full path and name of this file in the classpath, rather than just the name of the directory it is contained within.
Java Documentation
You may optionally download the Java documentation, which includes API pages that explain in good detail how each Java class can be used.
Etiquetas:
installing java,
java,
java development
How to configure DNS for Internet access in Windows Server 2003
This step-by-step guide describes how to configure Domain Name System (DNS) for Internet access in the Windows Server2003 products. DNS is the core name resolution tool that is used on the Internet. DNS handles resolution between host names and Internet addresses.
Back to the top
How to Start with a Stand-Alone Server Running Windows Server 2003
The stand-alone server running Windows Server 2003 becomes a DNS server for your network. In the first step, you assign this server a static Internet Protocol (IP) address. DNS servers must not use dynamically assigned IP addresses because a dynamic change of address could cause clients to lose contact with the DNS server.
Step 1: Configure TCP/IP
Click Start, point to Control Panel, point to Network Connections, and then click Local Area Connection.
Click Properties.
Click Internet Protocol (TCP/IP), and then click Properties.
Click the General tab.
Click Use the following IP address, and then type the IP address, subnet mask, and default gateway address in the appropriate boxes.
Click Advanced, and then click the DNS tab.
Click Append primary and connection specific DNS suffixes.
Click to select the Append parent suffixes of the primary DNS suffix check box.
Click to select the Register this connection's addresses in DNS check box.
Note that DNS servers running Windows Server 2003 must point to themselves for DNS. If this server needs to resolve names from its Internet service provider (ISP), you must configure a forwarder. Forwarders are discussed in the How to Configure Forwarders section later in this article.
Click OK three times.
NOTE: If you receive a warning from the DNS Caching Resolver service, click OK to dismiss the warning. The caching resolver is trying to contact the DNS server, but you have not finished configuring the server.
Step 2: Install Microsoft DNS Server
Click Start, point to Control Panel, and then click Add or Remove Programs.
Click Add or Remove Windows Components.
In the Components list, click Networking Services (but do not select or clear the check box), and then click Details.
Click to select the Domain Name System (DNS) check box, and then click OK.
Click Next.
When you are prompted, insert the Windows Server 2003 CD-ROM into the computer's CD-ROM or DVD-ROM drive.
On the Completing the Windows Components Wizard page, click Finish when Setup is complete.
Click Close to close the Add or Remove Programs window.
Step 3: Configure the DNS Server
To configure DNS by using the DNS snap-in in Microsoft Management Console (MMC), follow these steps:
Click Start, point to Programs, point to Administrative Tools, and then click DNS.
Right-click Forward lookup zones, and then click New Zone
When the New Zone Wizard starts, click Next.
You are prompted for a zone type. The zone types include:
Primary zone: Creates a copy of a zone that can be updated directly on this server. This zone information is stored in a .dns text file.
Secondary zone: A standard secondary zone copies all of the information from its master DNS server. A master DNS server can be an Active Directory, primary, or secondary zone that is configured for zone transfers. Note that you cannot modify the zone data on a secondary DNS server. All of its data is copied from its master DNS server.
Stub zone: A Stub zone contains only those resource records that are necessary to identify the authoritative DNS servers for that zone. Those resource records include Name Server (NS), Start of Authority (SOA), and possibly glue Host (A) records.
There is also an option to the store zone in Active Directory. This option is only available if the DNS server is a Domain controller.
The new forward lookup zone must be a primary or an Active Directory-integrated zone so that it can accept dynamic updates. Click Primary, and then click Next.
The new zone contains the locator records for this Active Directory-based domain. The name of the zone must be the same as the name of the Active Directory-based domain, or be a logical DNS container for that name. For example, if the Active Directory-based domain is named "support.microsoft.com", valid zone names are "support.microsoft.com" only.
Accept the default name for the new zone file. Click Next.
NOTE: Experienced DNS administrators may want to create a reverse lookup zone, and are encouraged to explore this branch of the wizard. A DNS server can resolve two basic requests: a forward lookup and a reverse lookup. A forward lookup is more common. A forward lookup resolves a host name to an IP address with an "A" or Host Resource record. A reverse lookup resolves an IP address to a host name with a PTR or Pointer Resource record. If you have your reverse DNS zones configured, you can automatically create associated reverse records when you create your original forward record.
How to Remove the Root DNS Zone
A DNS server running Windows Server 2003 follows specific steps in its name-resolution process. A DNS server first queries its cache, it checks its zone records, it sends requests to forwarders, and then it tries resolution by using root servers.
By default, a Microsoft DNS server connects to the Internet to process DNS requests more with root hints. When you use the Dcpromo tool to promote a server to a domain controller, the domain controller requires DNS. If you install DNS during the promotion process, a root zone is created. This root zone indicates to your DNS server that it is a root Internet server. Therefore, your DNS server does not use forwarders or root hints in the name-resolution process.
Click Start, point to Administrative Tools, and then click DNS.
Expand ServerName, where ServerName is the name of the server, click Properties and then expand Forward Lookup Zones.
Right-click the "." zone, and then click Delete.
How to Configure Forwarders
Windows Server 2003 can take advantage of DNS forwarders. This feature forwards DNS requests to external servers. If a DNS server cannot find a resource record in its zones, it can send the request to another DNS server for additional attempts at resolution. A common scenario might be to configure forwarders to your ISP's DNS servers.
Click Start, point to Administrative Tools, and then click DNS.
Right-click ServerName, where ServerName is the name of the server, and then click the Forwarders tab.
Click a DNS domain in the DNS domain list. Or, click New, type the name of the DNS domain for which you want to forward queries in the DNS domain box, and then click OK.
In the Selected domain's forwarder IP address box, type the IP address of the first DNS server to which you want to forward, and then click Add.
Repeat step 4 to add the DNS servers to which you want to forward.
Click OK.
How to Configure Root Hints
Windows can use root hints. The Root Hints resource records can be stored in either Active Directory or in a text file (%SystemRoot%\System32\DNS\Cache.dns). Windows uses the standard Internic root server. Also, when a server running Windows Server 2003 queries a root server, it updates itself with the most recent list of root servers.
Click Start, point to Administrative Tools, and then click DNS.
Right-click ServerName, where ServerName is the name of the server, and then click Properties.
Click the Root Hints tab. The DNS server's root servers are listed in the Name servers list.
If the Root Hints tab is unavailable, your server is still configured as a root server. See the How to Remove the Root DNS Zone section earlier in this article. You may have to use custom root hints that are different from the default. However, a configuration that points to the same server for root hints is always incorrect. Do not modify your root hints. If your root hints are incorrect and have to be replaced, click the following article number to view the article in the Microsoft Knowledge Base:
237675 (http://support.microsoft.com/kb/237675/ ) Setting up the Domain Name System for Active Directory
How to Configure DNS Behind a Firewall
Proxy and Network Address Translation (NAT) devices can restrict access to ports. DNS uses UDP port 53 and TCP port 53. The DNS Service Management console also uses RCP. RCP uses port 135. These are potential issues that may occur when you configure DNS and firewalls.
Back to the top
How to Start with a Stand-Alone Server Running Windows Server 2003
The stand-alone server running Windows Server 2003 becomes a DNS server for your network. In the first step, you assign this server a static Internet Protocol (IP) address. DNS servers must not use dynamically assigned IP addresses because a dynamic change of address could cause clients to lose contact with the DNS server.
Step 1: Configure TCP/IP
Click Start, point to Control Panel, point to Network Connections, and then click Local Area Connection.
Click Properties.
Click Internet Protocol (TCP/IP), and then click Properties.
Click the General tab.
Click Use the following IP address, and then type the IP address, subnet mask, and default gateway address in the appropriate boxes.
Click Advanced, and then click the DNS tab.
Click Append primary and connection specific DNS suffixes.
Click to select the Append parent suffixes of the primary DNS suffix check box.
Click to select the Register this connection's addresses in DNS check box.
Note that DNS servers running Windows Server 2003 must point to themselves for DNS. If this server needs to resolve names from its Internet service provider (ISP), you must configure a forwarder. Forwarders are discussed in the How to Configure Forwarders section later in this article.
Click OK three times.
NOTE: If you receive a warning from the DNS Caching Resolver service, click OK to dismiss the warning. The caching resolver is trying to contact the DNS server, but you have not finished configuring the server.
Step 2: Install Microsoft DNS Server
Click Start, point to Control Panel, and then click Add or Remove Programs.
Click Add or Remove Windows Components.
In the Components list, click Networking Services (but do not select or clear the check box), and then click Details.
Click to select the Domain Name System (DNS) check box, and then click OK.
Click Next.
When you are prompted, insert the Windows Server 2003 CD-ROM into the computer's CD-ROM or DVD-ROM drive.
On the Completing the Windows Components Wizard page, click Finish when Setup is complete.
Click Close to close the Add or Remove Programs window.
Step 3: Configure the DNS Server
To configure DNS by using the DNS snap-in in Microsoft Management Console (MMC), follow these steps:
Click Start, point to Programs, point to Administrative Tools, and then click DNS.
Right-click Forward lookup zones, and then click New Zone
When the New Zone Wizard starts, click Next.
You are prompted for a zone type. The zone types include:
Primary zone: Creates a copy of a zone that can be updated directly on this server. This zone information is stored in a .dns text file.
Secondary zone: A standard secondary zone copies all of the information from its master DNS server. A master DNS server can be an Active Directory, primary, or secondary zone that is configured for zone transfers. Note that you cannot modify the zone data on a secondary DNS server. All of its data is copied from its master DNS server.
Stub zone: A Stub zone contains only those resource records that are necessary to identify the authoritative DNS servers for that zone. Those resource records include Name Server (NS), Start of Authority (SOA), and possibly glue Host (A) records.
There is also an option to the store zone in Active Directory. This option is only available if the DNS server is a Domain controller.
The new forward lookup zone must be a primary or an Active Directory-integrated zone so that it can accept dynamic updates. Click Primary, and then click Next.
The new zone contains the locator records for this Active Directory-based domain. The name of the zone must be the same as the name of the Active Directory-based domain, or be a logical DNS container for that name. For example, if the Active Directory-based domain is named "support.microsoft.com", valid zone names are "support.microsoft.com" only.
Accept the default name for the new zone file. Click Next.
NOTE: Experienced DNS administrators may want to create a reverse lookup zone, and are encouraged to explore this branch of the wizard. A DNS server can resolve two basic requests: a forward lookup and a reverse lookup. A forward lookup is more common. A forward lookup resolves a host name to an IP address with an "A" or Host Resource record. A reverse lookup resolves an IP address to a host name with a PTR or Pointer Resource record. If you have your reverse DNS zones configured, you can automatically create associated reverse records when you create your original forward record.
How to Remove the Root DNS Zone
A DNS server running Windows Server 2003 follows specific steps in its name-resolution process. A DNS server first queries its cache, it checks its zone records, it sends requests to forwarders, and then it tries resolution by using root servers.
By default, a Microsoft DNS server connects to the Internet to process DNS requests more with root hints. When you use the Dcpromo tool to promote a server to a domain controller, the domain controller requires DNS. If you install DNS during the promotion process, a root zone is created. This root zone indicates to your DNS server that it is a root Internet server. Therefore, your DNS server does not use forwarders or root hints in the name-resolution process.
Click Start, point to Administrative Tools, and then click DNS.
Expand ServerName, where ServerName is the name of the server, click Properties and then expand Forward Lookup Zones.
Right-click the "." zone, and then click Delete.
How to Configure Forwarders
Windows Server 2003 can take advantage of DNS forwarders. This feature forwards DNS requests to external servers. If a DNS server cannot find a resource record in its zones, it can send the request to another DNS server for additional attempts at resolution. A common scenario might be to configure forwarders to your ISP's DNS servers.
Click Start, point to Administrative Tools, and then click DNS.
Right-click ServerName, where ServerName is the name of the server, and then click the Forwarders tab.
Click a DNS domain in the DNS domain list. Or, click New, type the name of the DNS domain for which you want to forward queries in the DNS domain box, and then click OK.
In the Selected domain's forwarder IP address box, type the IP address of the first DNS server to which you want to forward, and then click Add.
Repeat step 4 to add the DNS servers to which you want to forward.
Click OK.
How to Configure Root Hints
Windows can use root hints. The Root Hints resource records can be stored in either Active Directory or in a text file (%SystemRoot%\System32\DNS\Cache.dns). Windows uses the standard Internic root server. Also, when a server running Windows Server 2003 queries a root server, it updates itself with the most recent list of root servers.
Click Start, point to Administrative Tools, and then click DNS.
Right-click ServerName, where ServerName is the name of the server, and then click Properties.
Click the Root Hints tab. The DNS server's root servers are listed in the Name servers list.
If the Root Hints tab is unavailable, your server is still configured as a root server. See the How to Remove the Root DNS Zone section earlier in this article. You may have to use custom root hints that are different from the default. However, a configuration that points to the same server for root hints is always incorrect. Do not modify your root hints. If your root hints are incorrect and have to be replaced, click the following article number to view the article in the Microsoft Knowledge Base:
237675 (http://support.microsoft.com/kb/237675/ ) Setting up the Domain Name System for Active Directory
How to Configure DNS Behind a Firewall
Proxy and Network Address Translation (NAT) devices can restrict access to ports. DNS uses UDP port 53 and TCP port 53. The DNS Service Management console also uses RCP. RCP uses port 135. These are potential issues that may occur when you configure DNS and firewalls.
How to Configure Sendmail
Download Sendmail1Download Sendmail[1]. You may be automatically offered a short initial message which will indicate the current release. These instructions below assume version 8.10.0 or later.
2Build and install Sendmail for your machine. In most cases, this consists of unpacking the distribution, reading the README and sendmail/README files, and typing Build in the Sendmail directory. See the INSTALL file in the distribution's top-level directory for details.
Set up Sendmail1Understand that Sendmail uses information from the Domain Name System (DNS) to figure out which IP addresses go with which mailboxes.
2Choose an available domain name. In our example, we will use yourdomain.com.
3Configure your DNS on the server. Establish two machines as primary and secondary name servers for your domain. Knowledge of how to do this is assumed; otherwise, read the O'Reilly book "DNS and BIND", 4th Edition is highly recommended. Familiarize yourself with BIND before continuing.
4Configure MX records for your domain (Note: CNAME records can not be used; see § 5.2.2 of RFC 1123 for details.) MX records are explained in the O'Reilly Sendmail book; the 2nd edition gives an overview in § 15.3 and describes how to configure them in § 21.3, whereas the third edition explains everything about them in § 9.3. You have two options for MX records:
5Determine your connection method:
If the mail server which will serve your new domain has a full-time connection to the Internet, it should be the primary MX host for your domain. In this configuration, your MX records would look like this:
yourdomain.com. IN MX 10 yourmailserver.yourdomain.com.
Otherwise, you will need to find another machine to queue mail for your domain when you are not connected. Be sure to get the machine owners' approval first. That machine must be configured to allow relaying to your domain. If it is running Sendmail, this can be as simple as adding your domain to the relay-domains file on that machine. You would then point your MX records at that machine. For example:
yourdomain.com. IN MX 10 yourmailserver.yourdomain.com.
yourdomain.com. IN MX 20 othermailserver.otherdomain.com.
6Now the name servers are setup, register your domain using one of the registries. As you register, inform the registry of the two name servers, and then the domain will point to your server.
Configure Sendmail1Read the cf/README file thoroughly. It will give you instructions on creating a .mc file in the cf/cf directory. Your mailserver.mc file will typically look something like:
divert(-1)dnl
#
# This file contains the global definitions for yourdomain.com
#
divert(0)dnl
VERSIONID(`@(#)mailserver.mc 1.0 (yourdomain.com) 5/1/97')
OSTYPE(solaris2)dnl
DOMAIN(yourdomain.com)dnl
FEATURE(`virtusertable', `dbm /etc/mail/virtusertable')dnl
MAILER(local)dnl
MAILER(smtp)dnl
Your actual OS will be substituted for solaris2.
2A typical cf/domain/yourdomain.com.m4 file that looks something like:
divert(-1)dnl
#
# This file contains the global definitions for yourdomain.com
#
divert(0)dnl
VERSIONID(`@(#)yourdomain.com.m4 1.0 (yourdomain.com) 5/1/97')
FEATURE(`use_cw_file')dnl
3It may have some other feature()'s and define()'s as well. The virtual user table is the key to all of this.
4Generate your /etc/mail/sendmail.cf file from your mailserver.mc file, so type:
cd sendmail-VERSION/cf/cf
/Build mailserver.cf
cp mailserver.cf /etc/mail/sendmail.cf
5Create the virtual user table. This is explained in detail in the Sendmail book: § 19.6.28 of the 2nd edition, or § 4.8.51 of the 3rd edition; an overview is given here. The table is a database that maps virtual addresses into real addresses. You create a text file where each line has a key/value pair, separated by a TAB. For example:
Example 1:
joe@yourdomain.com jschmoe
jane@yourdomain.com jdoe@othercompany.com
@yourdomain.com jschmoe
In this first example, the address joe@yourdomain.com will be mapped to the local user jschmoe; jane@yourdomain.com will be mapped to the remote user jdoe@othercompany.com, and anything else coming in to yourdomain.com will also go to jschmoe.
Example 2:
joe@yourdomain.com jschmoe%3
bogus@yourdomain.com &npsp; error:nouser No such user here
list@yourdomain.com yourdomain-list
@yourdomain.com %1@othercompany.com
In this second example, the address joe@yourdomain.com will be mapped to the local user jschmoe%3 (see note 3 below for an explanation of what the %3 means), the address bogus@yourdomain.com will return the indicated error, the address list@yourdomain.com will be mapped to the local user yourdomain-list (which you would use the aliases file to ultimately resolve) and every other user at yourdomain.com will be mapped to a remote user of the same name at othercompany.com.
6If you have a local user, say sam, and there is no key for sam@yourdomain.com and no catch-all key for @yourdomain.com, then Sendmail will fall back to the local user sam when resolving sam@yourdomain.com. To prevent this, you must use either a catch-all key or an explicit key for sam@yourdomain.com; the error:nouser example above may be useful in this instance.
7If you want a virtual address to resolve to more than one real address, you need to do it indirectly. Have the virtual address resolve to a local alias, then have the local alias resolve to the desired set of addresses. For example, in the virtual user table:
joe@yourdomain.com localjoe
then in the aliases file:
localjoe: joe@othercompany.com, jane@othercompany.com
In the above example:
joe@yourdomain.com jschmoe%3
8The %3 is the preservation of the optional +detail part of the original address. In general, +detail means that when Sendmail gets an address like user+detail@domain, then if domain is in class w (see step 7 below), sendmail checks to see if user+detail can be resolved, then falls back to just plain user if not. Thus all of:
joe@yourdomain.com
joe+foo@yourdomain.com
joe+reallylongextrapart@yourdomain.com
would all match the above entry, with %3 preserving the +detail part of nothing, +foo and +reallylongextrapart respectively.
Multiple domains are allowed, and virtual addresses in each domain are independent. So for example, you could have:
joe@yourdomain1.com localjoe
joe@yourdomain2.com joe@othercompany.com
joe@yourdomain3.com localjoe
joe@yourdomain4.com error:nouser No such user here
9For people administering multiple domains, it may be easier to keep each domain's list in a separate file, then write a short script to concatenate all such files together into a master virtual user table. But we're getting ahead of ourselves; that's the next step...
Build the Sendmail User Table1Build the virtual user table. If the above virtual user table text file is located at sourcefile, and you are using the dbm database type, then use the command:
makemap dbm /etc/mail/virtusertable < sourcefile
Note: if you built Sendmail with NEWDB instead of NDBM, then use hash instead of dbm in the above line.
This creates one or more non-text files (typically /etc/mail/virtusertable.dir and /etc/mail/virtusertable.pag, or /etc/mail/virtusertable.db), but does not actually change /etc/mail/virtusertable itself, so this is the recommended location for sourcefile.
If you would like to reverse-map local users for out-bound mail, you will need to add support for the generics table to your .mc file:
FEATURE(`genericstable', `dbm /etc/mail/genericstable')dnl
GENERICS_DOMAIN_FILE(`/etc/mail/generics-domains')dnl
And you will need to create /etc/mail/genericstable which is like /etc/mail/virtusertable above except the columns are reversed:
jschmoe joe@yourdomain.com
Add your domain names to Sendmail1Add each new domain name to sendmail's class w. This is typically done by adding a line to /etc/mail/local-host-names (known as /etc/sendmail.cw prior to version 8.10) with the value of each domain name. Likewise, if you are using the genericstable, you should add any domains you wish to reverse-map to /etc/mail/generics-domains.
2Restart or SIGHUP sendmail.
3You do not need to restart sendmail when changing the virtual user or generics tables, only when changing /etc/mail/sendmail.cf or class files such as /etc/mail/local-host-names.
An extra step is required for hosts not connected full-time. As noted in the MX configuration section, if you use another host to queue your mail until you connect, you will have to force delivery of mail queued on the secondary mail server. To accomplish this, when your primary server connects, you should run the script etrn.pl which comes in the contrib directory of the sendmail distribution:
etrn.pl secondary-mx-host yourdomain.com
It may be advisable to put this at the end of the Sendmail start-up script on any primary MX. It would be especially useful as a follow-up to whatever script initiates the connection on primary MXs without full-time connections.
At this point, you should be set, and people should be able to send e-mail to addresses @yourdomain.com.
2Build and install Sendmail for your machine. In most cases, this consists of unpacking the distribution, reading the README and sendmail/README files, and typing Build in the Sendmail directory. See the INSTALL file in the distribution's top-level directory for details.
Set up Sendmail1Understand that Sendmail uses information from the Domain Name System (DNS) to figure out which IP addresses go with which mailboxes.
2Choose an available domain name. In our example, we will use yourdomain.com.
3Configure your DNS on the server. Establish two machines as primary and secondary name servers for your domain. Knowledge of how to do this is assumed; otherwise, read the O'Reilly book "DNS and BIND", 4th Edition is highly recommended. Familiarize yourself with BIND before continuing.
4Configure MX records for your domain (Note: CNAME records can not be used; see § 5.2.2 of RFC 1123 for details.) MX records are explained in the O'Reilly Sendmail book; the 2nd edition gives an overview in § 15.3 and describes how to configure them in § 21.3, whereas the third edition explains everything about them in § 9.3. You have two options for MX records:
5Determine your connection method:
If the mail server which will serve your new domain has a full-time connection to the Internet, it should be the primary MX host for your domain. In this configuration, your MX records would look like this:
yourdomain.com. IN MX 10 yourmailserver.yourdomain.com.
Otherwise, you will need to find another machine to queue mail for your domain when you are not connected. Be sure to get the machine owners' approval first. That machine must be configured to allow relaying to your domain. If it is running Sendmail, this can be as simple as adding your domain to the relay-domains file on that machine. You would then point your MX records at that machine. For example:
yourdomain.com. IN MX 10 yourmailserver.yourdomain.com.
yourdomain.com. IN MX 20 othermailserver.otherdomain.com.
6Now the name servers are setup, register your domain using one of the registries. As you register, inform the registry of the two name servers, and then the domain will point to your server.
Configure Sendmail1Read the cf/README file thoroughly. It will give you instructions on creating a .mc file in the cf/cf directory. Your mailserver.mc file will typically look something like:
divert(-1)dnl
#
# This file contains the global definitions for yourdomain.com
#
divert(0)dnl
VERSIONID(`@(#)mailserver.mc 1.0 (yourdomain.com) 5/1/97')
OSTYPE(solaris2)dnl
DOMAIN(yourdomain.com)dnl
FEATURE(`virtusertable', `dbm /etc/mail/virtusertable')dnl
MAILER(local)dnl
MAILER(smtp)dnl
Your actual OS will be substituted for solaris2.
2A typical cf/domain/yourdomain.com.m4 file that looks something like:
divert(-1)dnl
#
# This file contains the global definitions for yourdomain.com
#
divert(0)dnl
VERSIONID(`@(#)yourdomain.com.m4 1.0 (yourdomain.com) 5/1/97')
FEATURE(`use_cw_file')dnl
3It may have some other feature()'s and define()'s as well. The virtual user table is the key to all of this.
4Generate your /etc/mail/sendmail.cf file from your mailserver.mc file, so type:
cd sendmail-VERSION/cf/cf
/Build mailserver.cf
cp mailserver.cf /etc/mail/sendmail.cf
5Create the virtual user table. This is explained in detail in the Sendmail book: § 19.6.28 of the 2nd edition, or § 4.8.51 of the 3rd edition; an overview is given here. The table is a database that maps virtual addresses into real addresses. You create a text file where each line has a key/value pair, separated by a TAB. For example:
Example 1:
joe@yourdomain.com jschmoe
jane@yourdomain.com jdoe@othercompany.com
@yourdomain.com jschmoe
In this first example, the address joe@yourdomain.com will be mapped to the local user jschmoe; jane@yourdomain.com will be mapped to the remote user jdoe@othercompany.com, and anything else coming in to yourdomain.com will also go to jschmoe.
Example 2:
joe@yourdomain.com jschmoe%3
bogus@yourdomain.com &npsp; error:nouser No such user here
list@yourdomain.com yourdomain-list
@yourdomain.com %1@othercompany.com
In this second example, the address joe@yourdomain.com will be mapped to the local user jschmoe%3 (see note 3 below for an explanation of what the %3 means), the address bogus@yourdomain.com will return the indicated error, the address list@yourdomain.com will be mapped to the local user yourdomain-list (which you would use the aliases file to ultimately resolve) and every other user at yourdomain.com will be mapped to a remote user of the same name at othercompany.com.
6If you have a local user, say sam, and there is no key for sam@yourdomain.com and no catch-all key for @yourdomain.com, then Sendmail will fall back to the local user sam when resolving sam@yourdomain.com. To prevent this, you must use either a catch-all key or an explicit key for sam@yourdomain.com; the error:nouser example above may be useful in this instance.
7If you want a virtual address to resolve to more than one real address, you need to do it indirectly. Have the virtual address resolve to a local alias, then have the local alias resolve to the desired set of addresses. For example, in the virtual user table:
joe@yourdomain.com localjoe
then in the aliases file:
localjoe: joe@othercompany.com, jane@othercompany.com
In the above example:
joe@yourdomain.com jschmoe%3
8The %3 is the preservation of the optional +detail part of the original address. In general, +detail means that when Sendmail gets an address like user+detail@domain, then if domain is in class w (see step 7 below), sendmail checks to see if user+detail can be resolved, then falls back to just plain user if not. Thus all of:
joe@yourdomain.com
joe+foo@yourdomain.com
joe+reallylongextrapart@yourdomain.com
would all match the above entry, with %3 preserving the +detail part of nothing, +foo and +reallylongextrapart respectively.
Multiple domains are allowed, and virtual addresses in each domain are independent. So for example, you could have:
joe@yourdomain1.com localjoe
joe@yourdomain2.com joe@othercompany.com
joe@yourdomain3.com localjoe
joe@yourdomain4.com error:nouser No such user here
9For people administering multiple domains, it may be easier to keep each domain's list in a separate file, then write a short script to concatenate all such files together into a master virtual user table. But we're getting ahead of ourselves; that's the next step...
Build the Sendmail User Table1Build the virtual user table. If the above virtual user table text file is located at sourcefile, and you are using the dbm database type, then use the command:
makemap dbm /etc/mail/virtusertable < sourcefile
Note: if you built Sendmail with NEWDB instead of NDBM, then use hash instead of dbm in the above line.
This creates one or more non-text files (typically /etc/mail/virtusertable.dir and /etc/mail/virtusertable.pag, or /etc/mail/virtusertable.db), but does not actually change /etc/mail/virtusertable itself, so this is the recommended location for sourcefile.
If you would like to reverse-map local users for out-bound mail, you will need to add support for the generics table to your .mc file:
FEATURE(`genericstable', `dbm /etc/mail/genericstable')dnl
GENERICS_DOMAIN_FILE(`/etc/mail/generics-domains')dnl
And you will need to create /etc/mail/genericstable which is like /etc/mail/virtusertable above except the columns are reversed:
jschmoe joe@yourdomain.com
Add your domain names to Sendmail1Add each new domain name to sendmail's class w. This is typically done by adding a line to /etc/mail/local-host-names (known as /etc/sendmail.cw prior to version 8.10) with the value of each domain name. Likewise, if you are using the genericstable, you should add any domains you wish to reverse-map to /etc/mail/generics-domains.
2Restart or SIGHUP sendmail.
3You do not need to restart sendmail when changing the virtual user or generics tables, only when changing /etc/mail/sendmail.cf or class files such as /etc/mail/local-host-names.
An extra step is required for hosts not connected full-time. As noted in the MX configuration section, if you use another host to queue your mail until you connect, you will have to force delivery of mail queued on the secondary mail server. To accomplish this, when your primary server connects, you should run the script etrn.pl which comes in the contrib directory of the sendmail distribution:
etrn.pl secondary-mx-host yourdomain.com
It may be advisable to put this at the end of the Sendmail start-up script on any primary MX. It would be especially useful as a follow-up to whatever script initiates the connection on primary MXs without full-time connections.
At this point, you should be set, and people should be able to send e-mail to addresses @yourdomain.com.
Etiquetas:
conguring sendmail,
mail,
sendmail,
server,
smtp
Configure SSH on your Cisco router
Most IT pros realize that using Telnet to manage routers, switches, and firewalls is insecure. Transmitted in clear text across a network, Telnet traffic basically publicizes any login usernames and passwords to any attackers out there listening—who can take advantage of that information to access a device as the network administrator.
The standard alternative to Telnet's lack of security is Secure Shell (SSH). Like Telnet, you can use SSH to enter IOS commands over a network or to copy files over the network to a device. But with SSH, which uses encryption and digital certificates, you don't have nearly as many security concerns.
There are two versions of Secure Shell: SSH1 and SSH2. Cisco IOS 12.1(3)T was the first version to support SSH1; however, it does require the Data Encryption Standard (DES) or triple DES (3DES) IPSec encryption version of the IOS.
Certain versions of IOS 12.3—12.3(4)T, 12.2(25)S, and 12.3(7)JA or later—were the first to support SSH2, which requires a version of the IOS that supports 3DES. IOS versions that support 3DES have k9 in the name of the file.
It's important to note that SSH1 and SSH2 are two entirely different protocols. SSH2 offers much more security, and I recommend using it whenever possible. However, even SSH1 is better than Telnet. It will protect you from the casual hacker who's trying to sniff passwords from your network.
The Cisco IOS offers both an SSH server and an SSH client. So you can connect to your router's SSH server from an SSH client, or you can connect your router's SSH client to another device that has an SSH server.
Let's start with how to configure SSH on a Cisco IOS router. This configuration process is also very similar on Cisco switches and firewalls. Before you begin, make sure you have the proper image that includes IPSec DES or 3DES encryption to make sure using SSH is possible.
For our example, I'm using a 2611 router running IOS version 12.2(15)T9 that includes 3DES encryption. The exact filename is c2600-ik9o3s3-mz.122-15.T9.bin.
First, make sure your router has a hostname by using the hostname command. Here's an example:
Router(config)# hostname TR-Router
TR-Router(config)#Next, configure a domain name on your router using the ip domain-name command. Here's an example:
TR-Router(config)# ip domain-name TechRepublic.com
TR-Router(config)#Then, create an RSA encryption key pair for the router to use for authentication and encryption of the SSH data. One of the questions you must answer during this process is the modulus size of the key. Make sure the key modulus is at least 768 bits. Here's an example:
TR-Router(config)# crypto key generate rsa
The name for the keys will be: TR-Router.TechRepublic.com
Choose the size of the key modulus in the range of 360 to 2048for your General Purpose Keys. Choosing a key modulus greater than512 may take a few minutes.
How many bits in the modulus [512]: 768
% Generating 768 bit RSA keys ...[OK]
TR-Router(config)#
*Mar 1 00:17:13.337: %SSH-5-ENABLED: SSH 1.5 has been enabled
TR-Router(config)#As you can see from this example, after the system generates the key, you'll receive a message that it has automatically enabled SSH 1.5 on the router. To clarify, SSH 1.5 is Cisco's way of saying this router is running SSH1. If the system has enabled support for both SSH1 and SSH2, this message would say SSH 1.99. If the system has only enabled support for SSH2, the message would say SSH 2.0.
You can also configure SSH settings if you choose. To do so, use the ip ssh command with whichever parameters you choose to set. (Different IOS versions have different options because they support different versions of SSH.) Here's an example:
TR-Router(config)# ip ssh ?
authentication-retries Specify number of authentication retries
Port Starting (or only) port number to listen
on
Rsa Configure RSA keypair name for SSH
source-interface Specify interface for source address in SSH
connections
time-out Specify SSH time-out interval
TR-Router(config)# ip sshConfiguring optional SSH settings completes the process of configuring SSH on the router. Now, let's take a look at showing the SSH status.
To view the status of SSH, you can use the following commands:
Use show ip ssh to view SSH settings.
Use show ssh to view SSH connections.
Here's an example:
TR-Router# show ip ssh
SSH Enabled - version 1.5
Authentication timeout: 120 secs; Authentication retries: 3
TR-Router# show ssh
%No SSH server connections running.
TR-Router#SSH debug commands are also available by using the debug ip ssh command.
You can use a device's built-in SSH client to connect to other SSH servers. The Privileged Mode command is ssh. Here's an example:
TR-Router# ssh ? -c Select encryption algorithm -l Log in using this username -o Specify options -p Connect to this port WORD IP address or hostname of a remote system
TR-Router# sshOne word of caution: In May 2005, researchers discovered vulnerabilities in a number of Cisco IOS versions with SSH capabilities. For more information—and to make sure the IOS version you're using isn't vulnerable—check out "Cisco Security Advisory: Vulnerabilities in Cisco IOS Secure Shell Server."
Earlier in the article, I mentioned that you can also use SSH's secure functionality to copy files over your network. While space constraints keep me from delving further into the topic, check out Cisco's Secure Copy documentation for more information. For more information about configuring SSH on your router, check out Cisco's Configuring Secure Shell documentation and its Secure Shell Version 2 Support documentation.
Miss a column?
Check out the Cisco Routers and Switches Archive, and catch up on David Davis' most recent columns.
Want to learn more about router and switch management? Automatically sign up for our free Cisco Routers and Switches newsletter, delivered each Friday!
David Davis has worked in the IT industry for 12 years and holds several certifications, including CCIE, MCSE+I, CISSP, CCNA, CCDA, and CCNP. He currently manages a group of systems/network administrators for a privately owned retail company and performs networking/systems consulting on a part-time basis.
The standard alternative to Telnet's lack of security is Secure Shell (SSH). Like Telnet, you can use SSH to enter IOS commands over a network or to copy files over the network to a device. But with SSH, which uses encryption and digital certificates, you don't have nearly as many security concerns.
There are two versions of Secure Shell: SSH1 and SSH2. Cisco IOS 12.1(3)T was the first version to support SSH1; however, it does require the Data Encryption Standard (DES) or triple DES (3DES) IPSec encryption version of the IOS.
Certain versions of IOS 12.3—12.3(4)T, 12.2(25)S, and 12.3(7)JA or later—were the first to support SSH2, which requires a version of the IOS that supports 3DES. IOS versions that support 3DES have k9 in the name of the file.
It's important to note that SSH1 and SSH2 are two entirely different protocols. SSH2 offers much more security, and I recommend using it whenever possible. However, even SSH1 is better than Telnet. It will protect you from the casual hacker who's trying to sniff passwords from your network.
The Cisco IOS offers both an SSH server and an SSH client. So you can connect to your router's SSH server from an SSH client, or you can connect your router's SSH client to another device that has an SSH server.
Let's start with how to configure SSH on a Cisco IOS router. This configuration process is also very similar on Cisco switches and firewalls. Before you begin, make sure you have the proper image that includes IPSec DES or 3DES encryption to make sure using SSH is possible.
For our example, I'm using a 2611 router running IOS version 12.2(15)T9 that includes 3DES encryption. The exact filename is c2600-ik9o3s3-mz.122-15.T9.bin.
First, make sure your router has a hostname by using the hostname command. Here's an example:
Router(config)# hostname TR-Router
TR-Router(config)#Next, configure a domain name on your router using the ip domain-name command. Here's an example:
TR-Router(config)# ip domain-name TechRepublic.com
TR-Router(config)#Then, create an RSA encryption key pair for the router to use for authentication and encryption of the SSH data. One of the questions you must answer during this process is the modulus size of the key. Make sure the key modulus is at least 768 bits. Here's an example:
TR-Router(config)# crypto key generate rsa
The name for the keys will be: TR-Router.TechRepublic.com
Choose the size of the key modulus in the range of 360 to 2048for your General Purpose Keys. Choosing a key modulus greater than512 may take a few minutes.
How many bits in the modulus [512]: 768
% Generating 768 bit RSA keys ...[OK]
TR-Router(config)#
*Mar 1 00:17:13.337: %SSH-5-ENABLED: SSH 1.5 has been enabled
TR-Router(config)#As you can see from this example, after the system generates the key, you'll receive a message that it has automatically enabled SSH 1.5 on the router. To clarify, SSH 1.5 is Cisco's way of saying this router is running SSH1. If the system has enabled support for both SSH1 and SSH2, this message would say SSH 1.99. If the system has only enabled support for SSH2, the message would say SSH 2.0.
You can also configure SSH settings if you choose. To do so, use the ip ssh command with whichever parameters you choose to set. (Different IOS versions have different options because they support different versions of SSH.) Here's an example:
TR-Router(config)# ip ssh ?
authentication-retries Specify number of authentication retries
Port Starting (or only) port number to listen
on
Rsa Configure RSA keypair name for SSH
source-interface Specify interface for source address in SSH
connections
time-out Specify SSH time-out interval
TR-Router(config)# ip sshConfiguring optional SSH settings completes the process of configuring SSH on the router. Now, let's take a look at showing the SSH status.
To view the status of SSH, you can use the following commands:
Use show ip ssh to view SSH settings.
Use show ssh to view SSH connections.
Here's an example:
TR-Router# show ip ssh
SSH Enabled - version 1.5
Authentication timeout: 120 secs; Authentication retries: 3
TR-Router# show ssh
%No SSH server connections running.
TR-Router#SSH debug commands are also available by using the debug ip ssh command.
You can use a device's built-in SSH client to connect to other SSH servers. The Privileged Mode command is ssh. Here's an example:
TR-Router# ssh ? -c Select encryption algorithm -l Log in using this username -o Specify options -p Connect to this port WORD IP address or hostname of a remote system
TR-Router# sshOne word of caution: In May 2005, researchers discovered vulnerabilities in a number of Cisco IOS versions with SSH capabilities. For more information—and to make sure the IOS version you're using isn't vulnerable—check out "Cisco Security Advisory: Vulnerabilities in Cisco IOS Secure Shell Server."
Earlier in the article, I mentioned that you can also use SSH's secure functionality to copy files over your network. While space constraints keep me from delving further into the topic, check out Cisco's Secure Copy documentation for more information. For more information about configuring SSH on your router, check out Cisco's Configuring Secure Shell documentation and its Secure Shell Version 2 Support documentation.
Miss a column?
Check out the Cisco Routers and Switches Archive, and catch up on David Davis' most recent columns.
Want to learn more about router and switch management? Automatically sign up for our free Cisco Routers and Switches newsletter, delivered each Friday!
David Davis has worked in the IT industry for 12 years and holds several certifications, including CCIE, MCSE+I, CISSP, CCNA, CCDA, and CCNP. He currently manages a group of systems/network administrators for a privately owned retail company and performs networking/systems consulting on a part-time basis.
Etiquetas:
CISCO,
cisco router,
configure a router,
ssh cisco
Linux Hard Disk Format Command
Q. I've installed a new 250GB SATA hard disk on our office CentOS Linux server. How do I format a hard disk under Linux operating system from a shell prompt?
A.. There are total 4 steps involved for hard disk upgrade and installation procedure:
Step #1 : Partition the new disk using fdisk command
Following command will list all detected hard disks:
# fdisk -l | grep '^Disk'
Output:
Disk /dev/sda: 251.0 GB, 251000193024 bytes
Disk /dev/sdb: 251.0 GB, 251000193024 bytesA device name refers to the entire hard disk. For more information see Linux partition naming convention and IDE drive mappings.
To partition the disk - /dev/sdb, enter:
# fdisk /dev/sdb
The basic fdisk commands you need are:
m - print help
p - print the partition table
n - create a new partition
d - delete a partition
q - quit without saving changes
w - write the new partition table and exit
Step#2 : Format the new disk using mkfs.ext3 command
To format Linux partitions using ext2fs on the new disk:
# mkfs.ext3 /dev/sdb1
Step#3 : Mount the new disk using mount command
First create a mount point /disk1 and use mount command to mount /dev/sdb1, enter:
# mkdir /disk1
# mount /dev/sdb1 /disk1
# df -H
Step#4 : Update /etc/fstab file
Open /etc/fstab file, enter:
# vi /etc/fstab
Append as follows:
/dev/sdb1 /disk1 ext3 defaults 1 2Save and close the file.
Task: Label the partition
You can label the partition using e2label. For example, if you want to label the new partition /backup, enter
# e2label /dev/sdb1 /backup
You can use label name insted of partition name to mount disk using /etc/fstab:
LABEL=/backup /disk1 ext3 defaults 1 2
A.. There are total 4 steps involved for hard disk upgrade and installation procedure:
Step #1 : Partition the new disk using fdisk command
Following command will list all detected hard disks:
# fdisk -l | grep '^Disk'
Output:
Disk /dev/sda: 251.0 GB, 251000193024 bytes
Disk /dev/sdb: 251.0 GB, 251000193024 bytesA device name refers to the entire hard disk. For more information see Linux partition naming convention and IDE drive mappings.
To partition the disk - /dev/sdb, enter:
# fdisk /dev/sdb
The basic fdisk commands you need are:
m - print help
p - print the partition table
n - create a new partition
d - delete a partition
q - quit without saving changes
w - write the new partition table and exit
Step#2 : Format the new disk using mkfs.ext3 command
To format Linux partitions using ext2fs on the new disk:
# mkfs.ext3 /dev/sdb1
Step#3 : Mount the new disk using mount command
First create a mount point /disk1 and use mount command to mount /dev/sdb1, enter:
# mkdir /disk1
# mount /dev/sdb1 /disk1
# df -H
Step#4 : Update /etc/fstab file
Open /etc/fstab file, enter:
# vi /etc/fstab
Append as follows:
/dev/sdb1 /disk1 ext3 defaults 1 2Save and close the file.
Task: Label the partition
You can label the partition using e2label. For example, if you want to label the new partition /backup, enter
# e2label /dev/sdb1 /backup
You can use label name insted of partition name to mount disk using /etc/fstab:
LABEL=/backup /disk1 ext3 defaults 1 2
Etiquetas:
format dick,
hard disk format linux,
linux
How to Install Windows 7 on VMWare
You have just downloaded the new operating system: Windows 7, but you don't know how to install it. Well, install a new operating system is a little dangerous. Don't worry, you can use VMWare to do some experiments, if you like it, you can install it in your computer later.
Setup windows 7 in vmware
distribute disk space of windows 7 virtual machine
install windows 7 in VMware
accept the license
Solution
1. Install VMware first, then click "New Virtual Machine" to create a new virtual machine in VMWare.
Create a new virtual machine
2. Choose a type of configuration. In the following page, you can see "Typical" was selected by default.
Normally, you can click "Next" directly to "create a workstation 6.5 virtual machine in a few easy steps".
Setup windows 7 in vmware
3. Select "Install disc image file(iso)", then browse your disc image file of Windows 7, click "Next".
install windows 7 in VMware
4. Type your windows 7 product key and personalize information in the following dialog, include Full name, Password. Write down your Full name and Password, because it will be used for login to the Windows 7 Virtual Machine.
install windows 7 in VMware
5. Name your Windows 7 virtual machine, so as to others connect to your windows 7 virtual machine via local area network.
name the windows 7 virtual machine
6. Distribute Maxium disk size for your Windows 7, The Virtual machine's hard disk is stored as one or more files on the host computer's physical disk. These file(s) start small and become lager as your add applications, files, and data to your virtual machine.
The Maximum disk space must smaller than the disk whick the Windows 7 virtual machine will be located. Generally speaking, to install and use Windows 7, you'd better split more than 8GB in vmware disk. I recommand you distribute 16 GB by default.
Click "next".
distribute disk space of windows 7 virtual machine
7. Click "Finish" to start install Windows 7 virtual machine.
install windows 7 in VMware
Wait for a moment, VMWare will startup automatically. After virtual machine installation start, you will see the following dialog. Select your language, time'and currency format, keyboard or input method, then click "Next".
choose language of your Windows 7
Click "Install Now" to start install your Windows 7 virtual machine use VMware.
install windows 7 in VMware
Waiting for a moment. In the following picture, you can see Vmware is installing Windows 7 virtual machine for you.
install windows 7 in VMware
Read the license terms of install Windows 7 and accept it, then click "Next".Click Custom(advanced), but do not upgrade.
install windows 7 in VMware
Choose a hard drive to install your Windows 7. Then click "next". The hard drive must larger than "Maxium disk size" of your Windows 7 virtual machine.
Choose a hard drive to install windows 7 in VMwareIf you want to partition it, you can click "Drive options (advanced)".
Waiting for installing Windows 7 virtual machine, it will take you about 10 minutes.
setup windows 7 in vmware
After installing, Windows 7 virtual machine will be restarted automatically.windows 7 is starting
Wait for a moment. Setup is preparing your Windows 7 virtual machine for first use.
preparing your windows 7 virtual machine for first use
Type a username and computer name for your Windows 7 virtual machine, then click "next".
choose a username for your account in windows 7
Type a password twice for your Windows 7 virtual machine, then click "next"
set a password for your Windows 7 virtual machine
Type your windows 7 product key in the following dialog, then click "Next".
type windows 7 product key
Click Use recommended settings to protect your virtual computer and improve Windows 7 automatically.security settings of windows 7
Review time and date settings of Windows 7 virtual machine.set time and date of Windows 7
After a few minutes, you will see desktop of windows 7 display on your VMWare.
Windows 7 is finalizing settings.
Windows 7 VMware
Windows 7 virtual machine is preparing desktop.
Windows 7 virtual machine starting
Destop of Windows 7 virtual machine. Now you finished install Windows 7 virtual machine use VMware.
install windows 7 compeleted
Tips
You can also install windows Vista, Windows XP in VMware use this Tutorial.
Etiquetas:
virtual OS,
virtualization,
WMware
Suscribirse a:
Comentarios (Atom)